Web
Nmap Granny a web server on the target port 80
The running service is `Microsoft IIS httpd 6.0’
 Webroot
404 on the web root
Webroot
404 on the web root
 Wappalyzer identified technologies involved.
It uses ASP.NET
Wappalyzer identified technologies involved.
It uses ASP.NET
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/granny]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://$IP/FUZZ -ic -e .asp,.txt,.html -fc 302
________________________________________________
:: Method : GET
:: URL : http://10.10.10.15/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .asp .txt .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 302
________________________________________________
images [Status: 301, Size: 149, Words: 9, Lines: 2, Duration: 98ms]
_private [Status: 301, Size: 153, Words: 9, Lines: 2, Duration: 93ms]
postinfo.html [Status: 200, Size: 2440, Words: 327, Lines: 58, Duration: 94ms]
:: Progress: [882188/882188] :: Job [1/1] :: 427 req/sec :: Duration: [0:38:13] :: Errors: 240 ::ffuf discovered a file and directory; /_private/ and /postinfo.html
/_private/
 Directory Indexing is enabled, yet the
Directory Indexing is enabled, yet the /_private/ directory is empty
/postinfo.html
 The
The postinfo.html file appears to be a default HTML file generated by Microsoft FrontPage
Microsoft Frontpage was a web design software that was popular in the late 1990s and early 2000s. It was later replaced by by Microsoft Expression Web and SharePoint Designer
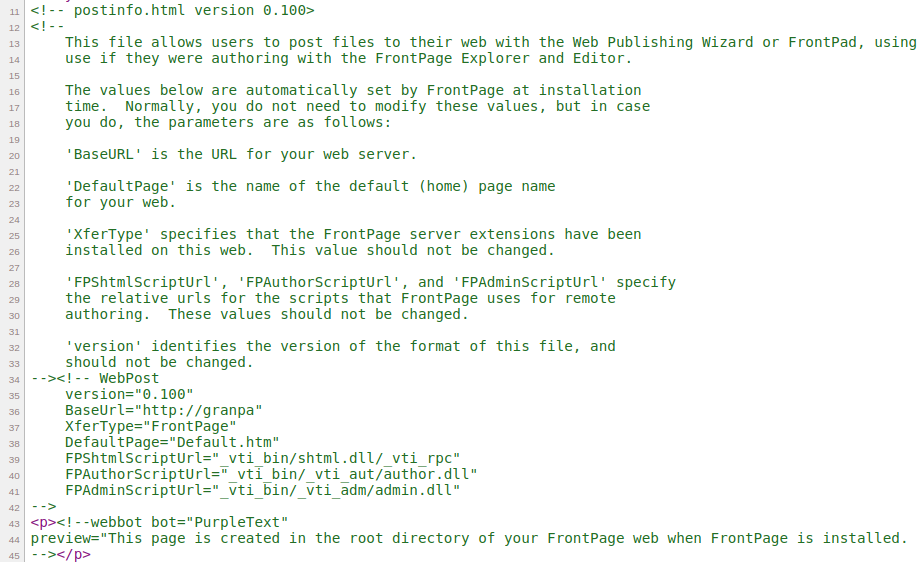 The source code contains comments that suggest it is used by the Web Publishing Wizard or FrontPad to allow users to post files to their web using the same username and password they would use if they were authoring with the FrontPage Explorer and Editor.
The source code contains comments that suggest it is used by the Web Publishing Wizard or FrontPad to allow users to post files to their web using the same username and password they would use if they were authoring with the FrontPage Explorer and Editor.
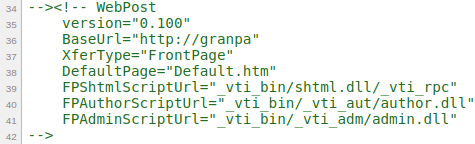 This section of the comment reveals some information about the target system.
The hostname appears to be
This section of the comment reveals some information about the target system.
The hostname appears to be granpa
There are some variables point to different files
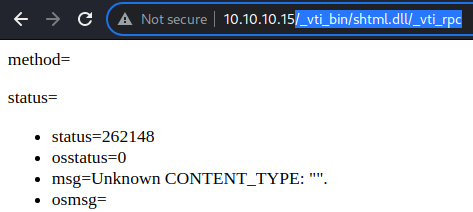
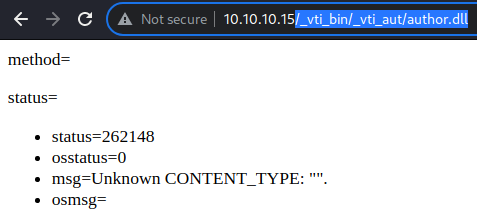
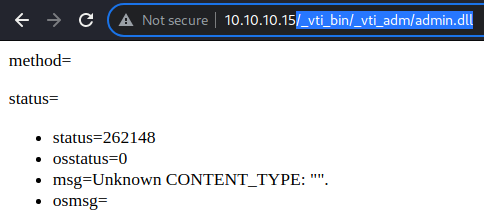 While I am not familiar with any of these as it is a very old technology, the output of all 3 files appears to be the same
While I am not familiar with any of these as it is a very old technology, the output of all 3 files appears to be the same
WebDAV
┌──(kali㉿kali)-[~/archive/htb/labs/granny]
└─$ nmap -Pn --script http-webdav* -p80 $IP
starting nmap 7.93 ( https://nmap.org ) at 2023-04-06 13:07 CEST
Nmap scan report for 10.10.10.15
Host is up (0.096s latency).
PORT STATE SERVICE
80/tcp open http
| http-webdav-scan:
| public options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| server type: Microsoft-IIS/6.0
| webdav type: Unknown
| allowed methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
|_ server date: Thu, 06 Apr 2023 11:07:25 GMT
nmap done: 1 IP address (1 host up) scanned in 1.15 secondsthe earlier nmap scan revealed that the target web server appears to have webdav enabled While I can clearly see that there are some potentially dangerous methods allowed by WebDAV, I will take a deeper dive into it
davtest
┌──(kali㉿kali)-[~/archive/htb/labs/granny]
└─$ davtest -url http://$IP/
********************************************************
Testing DAV connection
OPEN SUCCEED: http://10.10.10.15
********************************************************
NOTE Random string for this session: cXKfKDSxLFfnvce
********************************************************
Creating directory
MKCOL SUCCEED: Created http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce
********************************************************
Sending test files
PUT aspx FAIL
PUT shtml FAIL
PUT txt SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.txt
PUT html SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.html
PUT cfm SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.cfm
PUT cgi FAIL
PUT jsp SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.jsp
PUT jhtml SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.jhtml
PUT asp FAIL
PUT php SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.php
PUT pl SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.pl
********************************************************
Checking for test file execution
EXEC txt SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.txt
EXEC html SUCCEED: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.html
EXEC cfm FAIL
EXEC jsp FAIL
EXEC jhtml FAIL
EXEC php FAIL
EXEC pl FAIL
********************************************************
/usr/bin/davtest Summary:
Created: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce
PUT File: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.txt
PUT File: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.html
PUT File: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.cfm
PUT File: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.jsp
PUT File: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.jhtml
PUT File: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.php
PUT File: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.pl
Executes: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.txt
Executes: http://10.10.10.15/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.htmlUsing davtest, I can identify what method works and what method fails
Based on the result, only the txt and html extension got uploaded and executed successfully
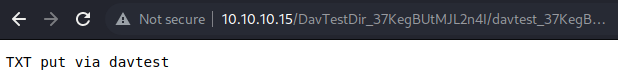
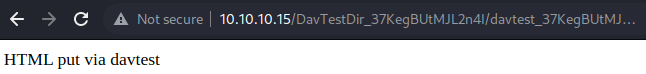
This can also be done manually using another WebDAV client tool, cadaver
cadaver
┌──(kali㉿kali)-[~/archive/htb/labs/granny]
└─$ cadaver http://$IP:80/
dav:/> ls
listing collection `/': succeeded.
coll: DavTestDir_cXKfKDSxLFfnvce 0 Apr 6 14:09
coll: _private 0 Apr 12 2017
coll: _vti_bin 0 Apr 12 2017
coll: _vti_cnf 0 Apr 12 2017
coll: _vti_log 0 Apr 12 2017
coll: _vti_pvt 0 Apr 12 2017
coll: _vti_script 0 Apr 12 2017
coll: _vti_txt 0 Apr 12 2017
coll: aspnet_client 0 Apr 12 2017
coll: images 0 Apr 12 2017
_vti_inf.html 1754 Apr 12 2017
iisstart.htm 1433 Feb 21 2003
pagerror.gif 2806 Feb 21 2003
postinfo.html 2440 Apr 12 2017I can see the /DavTestDir_37KegBUtMJL2n4I/ directory generated by davtest earlier
All that asides, I would need to upload executable extensions in order to achieve code execution by file upload
But that doesn’t seem to be available as davtest was not able to successfully either upload or execution such extensions; php, asp, aspx, and jsp
there are some ways around that.
renaming to executable
dav:/> cd DavTestDir_cXKfKDSxLFfnvce
dav:/DavTestDir_cXKfKDSxLFfnvce/> ls
Listing collection `/DavTestDir_cXKfKDSxLFfnvce/': succeeded.
davtest_cXKfKDSxLFfnvce.cfm 42 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.html 26 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.jhtml 37 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.jsp 37 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.php 24 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.pl 66 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.txt 19 Apr 6 14:08I can attempt to rename one of the uploaded files to the executable extensions such as asp or aspx
dav:/DavTestDir_cXKfKDSxLFfnvce/> move davtest_cXKfKDSxLFfnvce.txt davtest_cXKfKDSxLFfnvce.asp
Moving `/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.txt' to `/DavTestDir_cXKfKDSxLFfnvce/davtest_cXKfKDSxLFfnvce.asp': succeeded.
dav:/DavTestDir_cXKfKDSxLFfnvce/> ls
Listing collection `/DavTestDir_cXKfKDSxLFfnvce/': succeeded.
davtest_cXKfKDSxLFfnvce.asp 19 Apr 6 14:08
davtest_cXKfKDSxLFfnvce.cfm 42 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.html 26 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.jhtml 37 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.jsp 37 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.php 24 Apr 6 14:09
davtest_cXKfKDSxLFfnvce.pl 66 Apr 6 14:09So I changed the extension of the TXT file that I uploaded through davtest earlier to ASP and it worked.
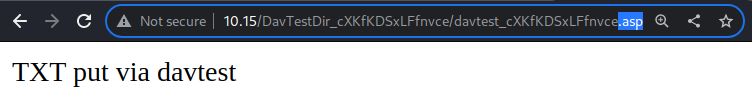 Give it a visit for confirmation. It is indeed loaded.
Give it a visit for confirmation. It is indeed loaded.
Moving on to the Exploitation phase